Overview
Volatility là một framework được dùng cho việc trích xuất thông tin ở trên tập tin bộ nhớ.
Memory Extraction
Trước khi phân tích tập tin bộ nhớ, ta cần xác định kiểu của nó. Một vài kiểu tập tin bộ nhớ của máy ảo:
- VMWare -
.vmem - Hyper-V -
.bin - Parallels -
.mem - VirtualBox -
.sav file(đây chỉ là một phần)
Plugins Overview
Với Volatility phiên bản 3, ta cần xác định hệ điều hành trước khi chỉ định plugin mà ta cần dùng chẳng hạn như windows.info hoặc linux.info. Đối với phiên bản 2, ta cần dùng plugin imageinfo để xác định.
Listing Processes and Connections
Để trích xuất tập tin PCAP từ tập tin bộ nhớ, ta có thể dùng plugin netstat:
python3 vol.py -f <file> windows.netstatTuy nhiên, plugin này không ổn định nên ta có thể dùng những công cụ khác chẳng hạn như bulk_extractor.
Volatility Hunting and Detection Capabilities
Plugin malfind sẽ cố gắng xác định các tiến trình bị chèn mã độc và PID của chúng. Ngoài ra, plugin này cũng xác định vùng bộ nhớ bị nhiễm mã đọc ở góc nhìn Hex, Ascii và Disassembly. Nó hoạt động bằng cách quét qua heap và xác định các tiến trình có bit thực thi là RWE hoặc RX nhưng không có tập tin tương ứng ở trên ổ đĩa (fileless malware).
Volatility cũng cung cấp khả năng để so sánh tập tin bộ nhớ với các quy luật YARA thông qua plugin yarascan.
Advanced Memory Forensics
Mã độc thường sử dụng hooking để không bị phát hiện, một số kỹ thuật hooking:
- SSDT Hooks
- IRP Hooks
- IAT Hooks
- EAT Hooks
- Inline Hooks
SSDT là viết tắt của System Service Descriptor Table, được sử dụng bởi Windows để tìm kiếm các hàm hệ thống. Mã độc có thể hook vào bảng này và chỉnh sửa các con trỏ tùy ý.
Volatility hỗ trợ plugin ssdt để phát hiện ra kỹ thuật này.
Ngoài ra còn có 2 plugin khác dùng để phát hiện các tập tin driver độc hại, thường được sử dụng bởi mã độc để không bị phát hiện:
modules: trích xuất danh sách các module có trong kerneldriverscan: trích xuất danh sách các driver hiện đang có mặt tại thời điểm tập tin bộ nhớ được sinh ra
Practical Investigations
Sử dụng plugin windows.info:
vol.py -f Investigation-1.vmem windows.info
Volatility 3 Framework 2.11.0
WARNING volatility3.framework.layers.vmware: No metadata file found alongside VMEM file. A VMSS or VMSN file may be required to correctly process a VMEM file. These should be placed in the same directory with the same file name, e.g. Investigation-1.vmem and Investigation-1.vmss.
Progress: 100.00 PDB scanning finished
Variable Value
Kernel Base 0x804d7000
DTB 0x2fe000
Symbols file:///home/aleister/Repos/volatility3/volatility3/symbols/windows/ntkrnlpa.pdb/30B5FB31AE7E4ACAABA750AA241FF331-1.json.xz
Is64Bit False
IsPAE True
layer_name 0 WindowsIntelPAE
memory_layer 1 FileLayer
KdDebuggerDataBlock 0x80545ae0
NTBuildLab 2600.xpsp.080413-2111
CSDVersion 3
KdVersionBlock 0x80545ab8
Major/Minor 15.2600
MachineType 332
KeNumberProcessors 1
SystemTime 2012-07-22 02:45:08+00:00
NtSystemRoot C:\WINDOWS
NtProductType NtProductWinNt
NtMajorVersion 5
NtMinorVersion 1
PE MajorOperatingSystemVersion 5
PE MinorOperatingSystemVersion 1
PE Machine 332
PE TimeDateStamp Sun Apr 13 18:31:06 2008What is the build version of the host machine in Case 001?
2600.xpsp.080413-2111
At what time was the memory file acquired in Case 001?
2012-07-22 02:45:08
Sử dụng plugin windows.psscan:
vol.py -f Investigation-1.vmem windows.psscan
Volatility 3 Framework 2.11.0
WARNING volatility3.framework.layers.vmware: No metadata file found alongside VMEM file. A VMSS or VMSN file may be required to correctly process a VMEM file. These should be placed in the same directory with the same file name, e.g. Investigation-1.vmem and Investigation-1.vmss.
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
908 652 svchost.exe 0x2029ab8 9 226 0 False 2012-07-22 02:42:33.000000 UTC N/A Disabled
664 608 lsass.exe 0x202a3b8 24 330 0 False 2012-07-22 02:42:32.000000 UTC N/A Disabled
652 608 services.exe 0x202ab28 16 243 0 False 2012-07-22 02:42:32.000000 UTC N/A Disabled
1640 1484 reader_sl.exe 0x207bda0 5 39 0 False 2012-07-22 02:42:36.000000 UTC N/A Disabled
1512 652 spoolsv.exe 0x20b17b8 14 113 0 False 2012-07-22 02:42:36.000000 UTC N/A Disabled
1588 1004 wuauclt.exe 0x225bda0 5 132 0 False 2012-07-22 02:44:01.000000 UTC N/A Disabled
788 652 alg.exe 0x22e8da0 7 104 0 False 2012-07-22 02:43:01.000000 UTC N/A Disabled
1484 1464 explorer.exe 0x23dea70 17 415 0 False 2012-07-22 02:42:36.000000 UTC N/A Disabled
1056 652 svchost.exe 0x23dfda0 5 60 0 False 2012-07-22 02:42:33.000000 UTC N/A Disabled
1136 1004 wuauclt.exe 0x23fcda0 8 173 0 False 2012-07-22 02:43:46.000000 UTC N/A Disabled
1220 652 svchost.exe 0x2495650 15 197 0 False 2012-07-22 02:42:35.000000 UTC N/A Disabled
608 368 winlogon.exe 0x2498700 23 519 0 False 2012-07-22 02:42:32.000000 UTC N/A Disabled
584 368 csrss.exe 0x24a0598 9 326 0 False 2012-07-22 02:42:32.000000 UTC N/A Disabled
368 4 smss.exe 0x24f1020 3 19 N/A False 2012-07-22 02:42:31.000000 UTC N/A Disabled
1004 652 svchost.exe 0x25001d0 64 1118 0 False 2012-07-22 02:42:33.000000 UTC N/A Disabled
824 652 svchost.exe 0x2511360 20 194 0 False 2012-07-22 02:42:33.000000 UTC N/A Disabled
4 0 System 0x25c89c8 53 240 N/A False N/A N/A DisabledWhat process can be considered suspicious in Case 001?
reader_sl.exebecause it hasexplorer.exeas parent process. Maybereader_sl.exehas been injected intoexplorer.exe.
What is the parent process of the suspicious process in Case 001?
explorer.exe
What is the PID of the suspicious process in Case 001?
1640
Trích xuất các tập tin PCAP từ tập tin bộ nhớ sử dụng bulk_extractor và tìm được một vài gói tin HTTP:
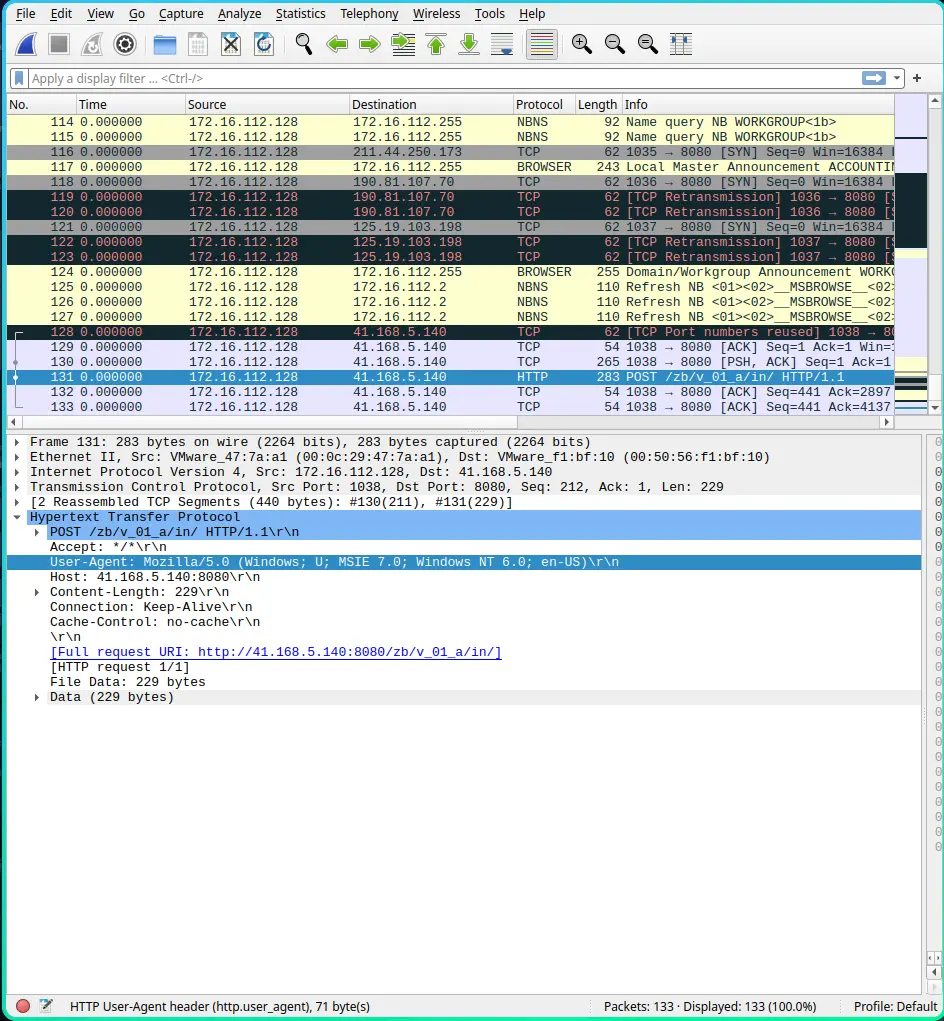
What user-agent was employed by the adversary in Case 001?
Mozilla/5.0 (Windows; U; MSIE 7.0; Windows NT 6.0; en-US)
Sử dụng strings để tìm chuỗi "http" và chuỗi "chase" ở trong Investigation-1.vmem:
strings Investigation-1.vmem | grep http |grep chase
action="https://mfasa.chase.com/auth/fcc/login" method="post" onsubmit="
<!-- BEGIN Global Navigation table --><table cellspacing="0" cellpadding="0" border="0" class="fullwidth" summary="global navigation"><tr><td><a href="http://www.chase.com/" id="siteLogo"><img src="https://chaseonline.chase.com/images//ChaseNew.gif" alt="Chase Online Logo" style="margin: 17px 17px 17px 17px;"/></a></td><td class="globalnav"><a id="homelink" href="JavaScript:document.location.href='http://www.chase.com/';" class="globalnavlinks">Chase.com</a> </td>
<td class="spacerw25"> <iframe name="ifr1" id="ifr1" src="https://www.chase.com/online/Home/images/chaseNewlogo.gif" frameborder="0" width="1px" height="1px" style="display:none"></iframe></td>Was Chase Bank one of the suspicious bank domains found in Case 001? (Y/N)
Y
Sử dụng plugin windows.psscan:
vol.py -f Investigation-2.raw windows.psscan
Volatility 3 Framework 2.11.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime File output
860 1940 taskdl.exe 0x1f4daf0 0 - 0 False 2017-05-12 21:26:23.000000 UTC 2017-05-12 21:26:23.000000 UTC Disabled
536 1940 taskse.exe 0x1f53d18 0 - 0 False 2017-05-12 21:26:22.000000 UTC 2017-05-12 21:26:23.000000 UTC Disabled
424 1940 @WanaDecryptor@ 0x1f69b50 0 - 0 False 2017-05-12 21:25:52.000000 UTC 2017-05-12 21:25:53.000000 UTC Disabled
1768 1024 wuauclt.exe 0x1f747c0 7 132 0 False 2017-05-12 21:22:52.000000 UTC N/A Disabled
576 1940 @WanaDecryptor@ 0x1f8ba58 0 - 0 False 2017-05-12 21:26:22.000000 UTC 2017-05-12 21:26:23.000000 UTC Disabled
260 664 svchost.exe 0x1fb95d8 5 105 0 False 2017-05-12 21:22:18.000000 UTC N/A Disabled
740 1940 @WanaDecryptor@ 0x1fde308 2 70 0 False 2017-05-12 21:22:22.000000 UTC N/A Disabled
1168 1024 wscntfy.exe 0x1fea8a0 1 37 0 False 2017-05-12 21:22:56.000000 UTC N/A Disabled
544 664 alg.exe 0x2010020 6 101 0 False 2017-05-12 21:22:55.000000 UTC N/A Disabled
1084 664 svchost.exe 0x203b7a8 6 72 0 False 2017-05-12 21:22:03.000000 UTC N/A Disabled
596 348 csrss.exe 0x2161da0 12 352 0 False 2017-05-12 21:22:00.000000 UTC N/A Disabled
348 4 smss.exe 0x2169020 3 19 N/A False 2017-05-12 21:21:55.000000 UTC N/A Disabled
620 348 winlogon.exe 0x216e020 23 536 0 False 2017-05-12 21:22:01.000000 UTC N/A Disabled
676 620 lsass.exe 0x2191658 23 353 0 False 2017-05-12 21:22:01.000000 UTC N/A Disabled
664 620 services.exe 0x21937f0 15 265 0 False 2017-05-12 21:22:01.000000 UTC N/A Disabled
1024 664 svchost.exe 0x21af7e8 79 1366 0 False 2017-05-12 21:22:03.000000 UTC N/A Disabled
904 664 svchost.exe 0x21b5230 9 227 0 False 2017-05-12 21:22:03.000000 UTC N/A Disabled
1152 664 svchost.exe 0x21bea78 10 173 0 False 2017-05-12 21:22:06.000000 UTC N/A Disabled
1636 1608 explorer.exe 0x21d9da0 11 331 0 False 2017-05-12 21:22:10.000000 UTC N/A Disabled
1484 664 spoolsv.exe 0x21e2da0 14 124 0 False 2017-05-12 21:22:09.000000 UTC N/A Disabled
1940 1636 tasksche.exe 0x2218da0 7 51 0 False 2017-05-12 21:22:14.000000 UTC N/A Disabled
836 664 svchost.exe 0x221a2c0 19 211 0 False 2017-05-12 21:22:02.000000 UTC N/A Disabled
1956 1636 ctfmon.exe 0x2231da0 1 86 0 False 2017-05-12 21:22:14.000000 UTC N/A Disabled
4 0 System 0x23c8830 51 244 N/A False N/A N/A DisabledWhat suspicious process is running at PID 740 in Case 002?
@WanaDecryptor@
Sử dụng plugin windows.pstree:
vol.py -f Investigation-2.raw windows.pstree
Volatility 3 Framework 2.11.0
Progress: 100.00 PDB scanning finished
PID PPID ImageFileName Offset(V) Threads Handles SessionId Wow64 CreateTime ExitTime Audit Cmd Path
4 0 System 0x823c8830 51 244 N/A False N/A N/A - - -
* 348 4 smss.exe 0x82169020 3 19 N/A False 2017-05-12 21:21:55.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\smss.exe \SystemRoot\System32\smss.exe \SystemRoot\System32\smss.exe
** 620 348 winlogon.exe 0x8216e020 23 536 0 False 2017-05-12 21:22:01.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\winlogon.exe winlogon.exe \??\C:\WINDOWS\system32\winlogon.exe
* 664 620 services.exe 0x821937f0 15 265 0 False 2017-05-12 21:22:01.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\services.exe C:\WINDOWS\system32\services.exe C:\WINDOWS\system32\services.exe
** 1024 664 svchost.exe 0x821af7e8 79 1366 0 False 2017-05-12 21:22:03.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\System32\svchost.exe -k netsvcs C:\WINDOWS\System32\svchost.exe
*** 1768 1024 wuauclt.exe 0x81f747c0 7 132 0 False 2017-05-12 21:22:52.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\wuauclt.exe "C:\WINDOWS\system32\wuauclt.exe" /RunStoreAsComServer Local\[400]SUSDS81a6658cb72fa845814e75cca9a42bf2 C:\WINDOWS\system32\wuauclt.exe
*** 1168 1024 wscntfy.exe 0x81fea8a0 1 37 0 False 2017-05-12 21:22:56.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\wscntfy.exe C:\WINDOWS\system32\wscntfy.exe C:\WINDOWS\system32\wscntfy.exe
** 1152 664 svchost.exe 0x821bea78 10 173 0 False 2017-05-12 21:22:06.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService C:\WINDOWS\system32\svchost.exe
** 544 664 alg.exe 0x82010020 6 101 0 False 2017-05-12 21:22:55.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\alg.exe C:\WINDOWS\System32\alg.exe C:\WINDOWS\System32\alg.exe
** 836 664 svchost.exe 0x8221a2c0 19 211 0 False 2017-05-12 21:22:02.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\system32\svchost -k DcomLaunch C:\WINDOWS\system32\svchost.exe
** 260 664 svchost.exe 0x81fb95d8 5 105 0 False 2017-05-12 21:22:18.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\system32\svchost.exe -k LocalService C:\WINDOWS\system32\svchost.exe
** 904 664 svchost.exe 0x821b5230 9 227 0 False 2017-05-12 21:22:03.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\system32\svchost -k rpcss C:\WINDOWS\system32\svchost.exe
** 1484 664 spoolsv.exe 0x821e2da0 14 124 0 False 2017-05-12 21:22:09.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\spoolsv.exe C:\WINDOWS\system32\spoolsv.exe C:\WINDOWS\system32\spoolsv.exe
** 1084 664 svchost.exe 0x8203b7a8 6 72 0 False 2017-05-12 21:22:03.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\svchost.exe C:\WINDOWS\system32\svchost.exe -k NetworkService C:\WINDOWS\system32\svchost.exe
* 676 620 lsass.exe 0x82191658 23 353 0 False 2017-05-12 21:22:01.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\lsass.exe C:\WINDOWS\system32\lsass.exe
** 596 348 csrss.exe 0x82161da0 12 352 0 False 2017-05-12 21:22:00.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\csrss.exe C:\WINDOWS\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,3072,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ProfileControl=Off MaxRequestThreads=16 \??\C:\WINDOWS\system32\csrss.exe
1636 1608 explorer.exe 0x821d9da0 11 331 0 False 2017-05-12 21:22:10.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\explorer.exe C:\WINDOWS\Explorer.EXE C:\WINDOWS\Explorer.EXE
* 1956 1636 ctfmon.exe 0x82231da0 1 86 0 False 2017-05-12 21:22:14.000000 UTC N/A \Device\HarddiskVolume1\WINDOWS\system32\ctfmon.exe "C:\WINDOWS\system32\ctfmon.exe" C:\WINDOWS\system32\ctfmon.exe
* 1940 1636 tasksche.exe 0x82218da0 7 51 0 False 2017-05-12 21:22:14.000000 UTC N/A \Device\HarddiskVolume1\Intel\ivecuqmanpnirkt615\tasksche.exe "C:\Intel\ivecuqmanpnirkt615\tasksche.exe" C:\Intel\ivecuqmanpnirkt615\tasksche.exe
** 740 1940 @WanaDecryptor@ 0x81fde308 2 70 0 False 2017-05-12 21:22:22.000000 UTC N/A \Device\HarddiskVolume1\Intel\ivecuqmanpnirkt615\@WanaDecryptor@.exe @WanaDecryptor@.exe C:\Intel\ivecuqmanpnirkt615\@WanaDecryptor@.exeWhat is the full path of the suspicious binary in PID 740 in Case 002?
C:\Intel\ivecuqmanpnirkt615\@WanaDecryptor@.exe
What is the parent process of PID 740 in Case 002?
tasksche.exe
What is the suspicious parent process PID connected to the decryptor in Case 002?
1940
From our current information, what malware is present on the system in Case 002?
Wannacry
What DLL is loaded by the decryptor used for socket creation in Case 002?
Ws2_32.dll(just google¯\_( ͡° ͜ʖ ͡°)_/¯).
Sử dụng plugin windows.mutantscan:
vol.py -f Investigation-2.raw windows.mutantscan
Volatility 3 Framework 2.11.0
Progress: 100.00 PDB scanning finished
Offset Name
0x1f526a8 N/A
0x1f64a10 Instance0: ESENT Performance Data Schema Version 40
0x1f788c8 N/A
0x1f78908 N/A
0x1f7b858 N/A
0x1f7c7e8 RAS_MO_01
0x1f84a08 N/A
0x1f98a50 N/A
0x1f99b90 N/A
0x1fad800 N/A
0x1fb7fe0 N/A
0x1fbbda8 N/A
0x1fbbde8 N/A
0x1fbbe58 N/A
0x1fe49f8 N/A
0x1fe8200 N/A
0x1fee800 RAS_MO_02
0x1ffae30 N/A
0x200b4b0 N/A
0x200c860 N/A
0x2025728 MSCTF.Shared.MUTEX.IHG
0x202f800 MidiMapper_Configure
0x2030748 SRDataStore
0x20346c8 N/A
0x2084bd8 wscntfy_mtx
0x2084e10 N/A
0x2084e50 N/A
0x2087030 WPA_RT_MUTEX
0x2087b80 WPA_LICSTORE_MUTEX
0x2087bd0 WPA_HWID_MUTEX
0x2087c20 WPA_LT_MUTEX
0x2089680 N/A
0x208a270 N/A
0x215bb38 N/A
0x215c360 N/A
0x215c3a0 N/A
0x215c908 _SHuassist.mtx
0x2160580 N/A
0x216e558 N/A
0x216e598 N/A
0x216e5d8 N/A
0x216e618 N/A
0x216ea30 userenv: User Registry policy mutex
0x216ea80 userenv: user policy mutex
0x217f180 msgina: InteractiveLogonMutex
0x21883e8 ShimCacheMutex
0x2194a90 N/A
0x2197180 msgina: InteractiveLogonRequestMutex
0x21a20f8 N/A
0x21aded0 N/A
0x21b05d0 N/A
0x21b13c8 winlogon: Logon UserProfileMapping Mutex
0x21b3810 ZonesCounterMutex
0x21b4a10 N/A
0x21b5910 N/A
0x21b6e90 N/A
0x21b6ed0 N/A
0x21ba0b0 PnP_Init_Mutex
0x21bac38 CTF.LBES.MutexDefaultS-1-5-21-602162358-764733703-1957994488-1003
0x21bb348 CTF.Compart.MutexDefaultS-1-5-21-602162358-764733703-1957994488-1003
0x21bcd40 N/A
0x21bd030 RasPbFile
0x21bd440 N/A
0x21bd688 N/A
0x21bdab0 N/A
0x21be4f0 N/A
0x21bfaa0 SHIMLIB_LOG_MUTEX
0x21c03f8 N/A
0x21c4de0 N/A
0x21c4e20 N/A
0x21c7768 N/A
0x21cf578 N/A
0x21cf688 N/A
0x21cfab0 N/A
0x21cfed8 N/A
0x21d03f8 N/A
0x21d1640 N/A
0x21d1680 N/A
0x21d16d0 746bbf3569adEncrypt
0x21d6ad8 N/A
0x21d6b48 N/A
0x21d6bb8 N/A
0x21d6ed0 N/A
0x21d6f40 N/A
0x21d6fb0 N/A
0x21d7310 N/A
0x21d7380 N/A
0x21d73f0 N/A
0x21d7460 N/A
0x21d7778 N/A
0x21d77e8 N/A
0x21d7858 N/A
0x21d7b98 N/A
0x21d7ec8 N/A
0x21d8468 N/A
0x21d8878 N/A
0x21d88e8 N/A
0x21d9550 N/A
0x21dca88 N/A
0x21df4e0 N/A
0x21df7b0 N/A
0x21dfba8 N/A
0x21e0aa0 MsnSspcPrivatePwdMutex
0x21e34b0 ExplorerIsShellMutex
0x21e5330 N/A
0x21e5e48 N/A
0x21e6598 N/A
0x21e6608 N/A
0x21ed0a0 N/A
0x21ede50 N/A
0x21f00a8 N/A
0x21f07c8 N/A
0x21f2ea8 N/A
0x2212860 N/A
0x2214740 userenv: Machine Registry policy mutex
0x2214790 userenv: machine policy mutex
0x2219398 MSCTF.Shared.MUTEX.EBD
0x2219680 N/A
0x221f860 N/A
0x22292d8 CTF.TimListCache.FMPDefaultS-1-5-21-602162358-764733703-1957994488-1003MUTEX.DefaultS-1-5-21-602162358-764733703-1957994488-1003
0x2229b18 WindowsUpdateTracingMutex
0x222fea8 CtfmonInstMutexDefaultS-1-5-21-602162358-764733703-1957994488-1003
0x2232ea8 ZoneAttributeCacheCounterMutex
0x2233bb8 {A3BD3259-3E4F-428a-84C8-F0463A9D3EB5}
0x223a2d8 ZonesCacheCounterMutex
0x223e0e0 ZonesLockedCacheCounterMutex
0x223f180 N/A
0x22460e0 c:!documents and settings!localservice!local settings!temporary internet files!content.ie5!
0x2246238 c:!documents and settings!localservice!local settings!history!history.ie5!
0x2247de0 WininetProxyRegistryMutex
0x22480e0 _!MSFTHISTORY!_
0x2248bc8 N/A
0x22496c8 238FAD3109D3473aB4764B20B3731840
0x2249718 4FCC0DEFE22C4f138FB9D5AF25FD9398
0x2249768 0CADFD67AF62496dB34264F000F5624A
0x224d6b0 WininetStartupMutex
0x224d798 MSCTF.GCompartListMUTEX.DefaultS-1-5-21-602162358-764733703-1957994488-1003
0x224f180 MsWinZonesCacheCounterMutexA
0x22510a0 N/A
0x2251790 N/A
0x2254180 c:!documents and settings!localservice!cookies!
0x225f740 N/A
0x225f7b0 N/A
0x225f820 N/A
0x225f8f0 N/A
0x227b840 N/A
0x227cc18 N/A
0x227e258 SingleSesMutex
0x22cc940 WPA_PR_MUTEX
0x22e3b08 MsWinZonesCacheCounterMutexA0
0x22eba30 N/A
0x22eddb8 MidiMapper_modLongMessage_RefCnt
0x232a020 N/A
0x238b030 CTF.Asm.MutexDefaultS-1-5-21-602162358-764733703-1957994488-1003
0x238b090 CTF.TMD.MutexDefaultS-1-5-21-602162358-764733703-1957994488-1003
0x238b0e0 CTF.Layouts.MutexDefaultS-1-5-21-602162358-764733703-1957994488-1003Tuy nhiên, không dễ để biết mutant (một đối tượng của kernel cho phép các chương trình thực hiện đồng bộ hóa1) nào là bất thường.
Có thể sử dụng plugin windows.handles và grep 1940 với 1940 là PID của tasksche.exe
vol.py -f Investigation-2.raw windows.handles | grep 1940
596 csrss.exe 0x82218da0 0x388 Process 0x1f0fff tasksche.exe Pid 1940
596 csrss.exe 0x8222eda0 0x390 Thread 0x1f03ff Tid 1944 Pid 1940
596 csrss.exe 0x81fdd9f8 0x3f0 Thread 0x1f03ff Tid 500 Pid 1940
596 csrss.exe 0x81fdd640 0x400 Thread 0x1f03ff Tid 504 Pid 1940
596 csrss.exe 0x81fe72f8 0x458 Thread 0x1f03ff Tid 472 Pid 1940
596 csrss.exe 0x81fe3870 0x45c Thread 0x1f03ff Tid 468 Pid 1940
596 csrss.exe 0x81fa9b20 0x470 Thread 0x1f03ff Tid 488 Pid 1940
596 csrss.exe 0x81fa5640 0x478 Thread 0x1f03ff Tid 496 Pid 1940
676 lsass.exe 0x82218da0 0x4dc Process 0x478 tasksche.exe Pid 1940
1024 svchost.exe 0x82218da0 0xae8 Process 0x478 tasksche.exe Pid 1940
1024 svchost.exe 0x81f61940 0x1148 IoCompletion 0x1f0003
1940 tasksche.exe 0xe1005468 0x4 KeyedEvent 0xf0003 CritSecOutOfMemoryEvent
1940 tasksche.exe 0xe147f350 0x8 Directory 0x3 KnownDlls
1940 tasksche.exe 0x81fbce00 0xc File 0x100020 \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.6028_x-ww_61e65202
1940 tasksche.exe 0x8217cfa0 0x10 WindowStation 0xf037f WinSta0
1940 tasksche.exe 0xe15a9d50 0x14 Directory 0xf000f Windows
1940 tasksche.exe 0xe1b8a450 0x18 Port 0x21f0001
1940 tasksche.exe 0x82251428 0x1c Event 0x21f0003
1940 tasksche.exe 0x82365c80 0x20 Desktop 0xf01ff Default
1940 tasksche.exe 0x8217cfa0 0x24 WindowStation 0xf037f WinSta0
1940 tasksche.exe 0x821aa390 0x28 Semaphore 0x100003
1940 tasksche.exe 0x821aa358 0x2c Semaphore 0x100003
1940 tasksche.exe 0xe1a05938 0x30 Key 0x20f003f MACHINE
1940 tasksche.exe 0x82233f18 0x34 File 0x100020 \Device\HarddiskVolume1\Intel\ivecuqmanpnirkt615
1940 tasksche.exe 0xe1a67d48 0x38 Token 0x8
1940 tasksche.exe 0xe149f908 0x3c Directory 0x2000f BaseNamedObjects
1940 tasksche.exe 0x821883e8 0x40 Mutant 0x120001 ShimCacheMutex
1940 tasksche.exe 0xe16644e0 0x44 Section 0x2 ShimSharedMemory
1940 tasksche.exe 0x822386a8 0x48 File 0x100001 \Device\KsecDD
1940 tasksche.exe 0x823d54d0 0x4c Semaphore 0x1f0003 shell.{A48F1A32-A340-11D1-BC6B-00A0C90312E1}
1940 tasksche.exe 0x823a0cd0 0x50 File 0x100020 \Device\HarddiskVolume1\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.6028_x-ww_61e65202
1940 tasksche.exe 0x8224f180 0x54 Mutant 0x1f0001 MsWinZonesCacheCounterMutexA
1940 tasksche.exe 0x822e3b08 0x58 Mutant 0x1f0001 MsWinZonesCacheCounterMutexA0
1940 tasksche.exe 0x82234450 0x5c Event 0x1f0003
1940 tasksche.exe 0x821dbdd8 0x60 Semaphore 0x100003
1940 tasksche.exe 0x822398f8 0x64 Semaphore 0x100003
1940 tasksche.exe 0x8221da98 0x68 Semaphore 0x100003
1940 tasksche.exe 0x8221d9f0 0x6c Semaphore 0x100003
1940 tasksche.exe 0x8221da28 0x70 Semaphore 0x100003
1940 tasksche.exe 0x820146d8 0x74 Semaphore 0x100003
1940 tasksche.exe 0x81ff09f0 0x78 Semaphore 0x100003
1940 tasksche.exe 0x81ff0988 0x7c Semaphore 0x100003
1940 tasksche.exe 0x81ff0a58 0x80 Semaphore 0x100003
1940 tasksche.exe 0x81ff0b90 0x84 Semaphore 0x100003
1940 tasksche.exe 0x81ff0b28 0x88 Semaphore 0x100003
1940 tasksche.exe 0x81ff0c60 0x8c Semaphore 0x100003
1940 tasksche.exe 0x8225f5d8 0x90 Event 0x1f0003
1940 tasksche.exe 0x8223b668 0x94 Event 0x1f0003
1940 tasksche.exe 0x8215c330 0x98 Event 0x1f0003
1940 tasksche.exe 0x822555f0 0x9c Event 0x1f0003
1940 tasksche.exe 0x8222eda0 0xa0 Thread 0x1f03ff Tid 1944 Pid 1940
1940 tasksche.exe 0x8219d480 0xa4 IoCompletion 0x1f0003
1940 tasksche.exe 0x81fe7e88 0xa8 IoCompletion 0x1f0003
1940 tasksche.exe 0x8219d480 0xac IoCompletion 0x1f0003
1940 tasksche.exe 0x81fa9b20 0xb4 Thread 0x1f03ff Tid 488 Pid 1940
1940 tasksche.exe 0x81fdd640 0xb8 Thread 0x1f03ff Tid 504 Pid 1940
1940 tasksche.exe 0x821dea50 0xc0 Semaphore 0x1f0003 shell.{210A4BA0-3AEA-1069-A2D9-08002B30309D}
1940 tasksche.exe 0xe1b978d0 0xc4 Key 0x20f003f USER\S-1-5-21-602162358-764733703-1957994488-1003
1940 tasksche.exe 0x8219bde0 0xc8 Event 0x1f0003 userenv: User Profile setup event
1940 tasksche.exe 0xe1530470 0xd0 Port 0x1f0001
1940 tasksche.exe 0xe1a45cd8 0xe4 Port 0x1f0001
1940 tasksche.exe 0xe18c02d0 0xe8 Section 0x4What mutex can be found that is a known indicator of the malware in question in Case 002?
MsWinZonesCacheCounterMutexA
What plugin could be used to identify all files loaded from the malware working directory in Case 002?
windows.filescan
Related
list
from outgoing([[TryHackMe - Volatility]])
sort file.ctime ascResources
- TryHackMe | Volatility
- volatilityfoundation/volatility3: Volatility 3.0 development
- Volatility 3 — Volatility 3 2.11.0 documentation