Principles of Priviledges
Two key concepts are used to assign and manage the access rights of individuals: Privileged Identity Management (PIM) and Privileged Access Management (or PAM for short).
Initially, these two concepts can seem to overlap; however, they are different from one another. PIM is used to translate a user’s role within an organization into an access role on a system. Whereas PAM is the management of the privileges a system’s access role has, amongst other things.
PAM also encompasses enforcing security policies such as password management, auditing policies and reducing the attack surface a system faces.
Security Models
According to a security model, any system or piece of technology storing information is called an information system, which is how we will reference systems and devices in this task.
Bell and LaPadula Model
The Bell-La Padula Model is used to achieve confidentiality. This model has a few assumptions, such as an organization’s hierarchical structure it is used in, where everyone’s responsibilities/roles are well-defined.
This model uses the rule “no write down, no read up”.

The Bell LaPadula Model is popular within organizations such as governmental and military because it was first created as a way to enforce different levels of access for government organizations that deal with highly classified organizations
Biba Model
The Biba model is arguably the equivalent of the Bell-La Padula model but for the integrity of the CIA triad.
This model applies the rule to objects (data) and subjects (users) that can be summarised as “no write up, no read down”. This rule means that subjects can create or write content to objects at or below their level but can only read the contents of objects above the subject’s level.
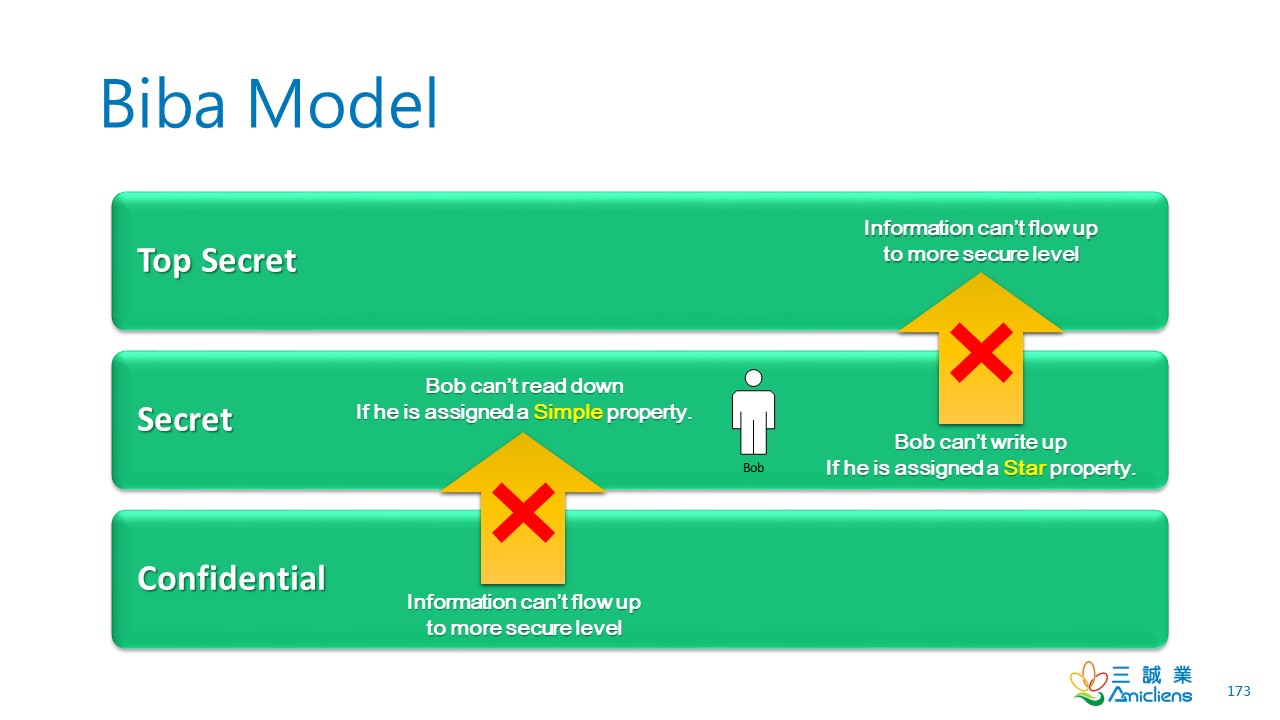
The Biba model is used in organizations or situations where integrity is more important than confidentiality. For example, in software development, developers may only have access to the code that is necessary for their job. They may not need access to critical pieces of information such as databases, etc.
Threat Modeling
Threat modelling is the process of reviewing, improving, and testing the security protocols in place in an organization’s information technology infrastructure and services.
A critical stage of the threat modelling process is identifying likely threats that an application or system may face, the vulnerabilities a system or application may be vulnerable to.
The principles of all threat modelling methodologies return to:
- Preparation
- Identification
- Mitigations
- Review
To help with this, there are frameworks such as STRIDE (Spoofing identity, Tampering with data, Repudiation threats, Information disclosure, Denial of Service and Elevation of privileges) and PASTA (Process for Attack Simulation and Threat Analysis)
Incident Response
A breach of security is known as an incident. And despite all rigorous threat models and secure system designs, incidents do happen. Actions taken to resolve and remediate the threat are known as Incident Response (IR) and are a whole career path in cybersecurity.
Incidents are classified using a rating of urgency and impact. Urgency will be determined by the type of attack faced, where the impact will be determined by the affected system and what impact that has on business operations.
To successfully solve an incident, these steps are often referred to as the six phases of Incident Response that takes place, that are:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned