At first, the attacker will use the IDA tool for static analysis. By searching through the export functions of the libwautils.dll module, the attacker can find a function named createAESWithOpswatSecret:
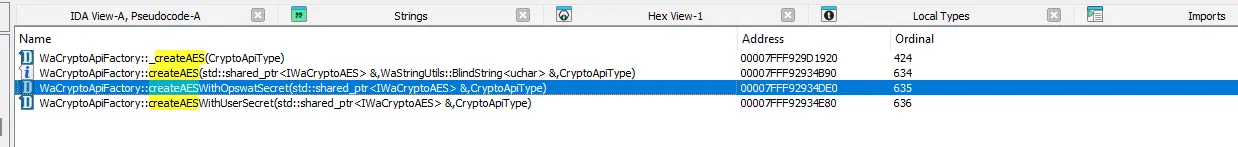
Decompile this function, he has the following pseudo code:
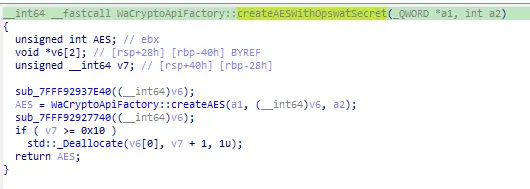
Continue decompiling the sub_7FFF92937E40 function, which is invoked at the beginning of the above function:
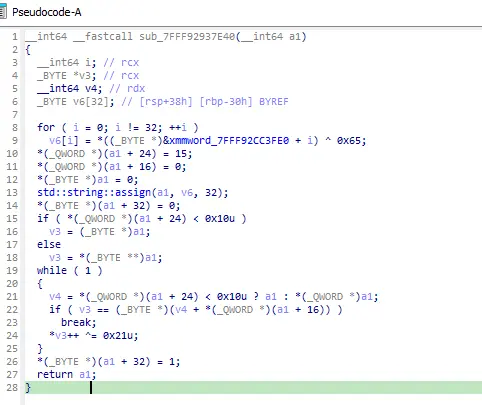
This function does something with xmmword_7FFF92CC3FE0 and by following the references to this value, we found another function named sub_7FFD52364280 that contains some hardcoded values:
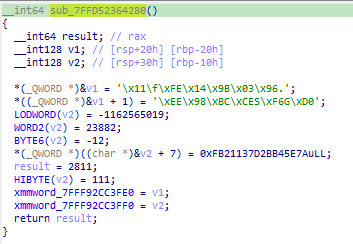
At this time, the attacker can conclude that the key is generated from some hardcoded values.
License Encryption
Decrypt license: AES Decrypt - CyberChef
Decrypted license:
{
"_id": "68c92048c1c57200172d67fe",
"user_id": "68c92048c1c57200172d67fc",
"timestamp": "1758091373",
"offline_mode": true,
"online_mode": true,
"pass_key_hashes": {
"_id": "68c920858c8523c8811826f9",
"user_id": "68c92048c1c57200172d67fc",
"timestamp": "1758091373",
"pass_keys": {
"c900809cdb059bc0a7c9ad015760aaaafbedcf3557bde6a49366c163446ffb34d9584d415dd4497ed6d5440171cbf6ff4a60744b1f50130da82141fa9e6a7061": "USER",
"a07253e0fec14e036b19947a4e2d7e8955b117ab68d168543a0c0bb62c62cbecada7344c6ecd3f49c186ba65b3044908c8035960683d4532c22013890f2346d7": "OPSWAT"
}
},
"gears_sdk_detection": {
"module_name": "detection",
"enabled": false,
"expiration": "0"
},
"gears_sdk_manageability": {
"module_name": "manageability",
"enabled": false,
"expiration": "0"
},
"gears_sdk_vulnerability": {
"module_name": "vulnerability",
"enabled": false,
"expiration": "0"
},
"gears_sdk_removal": {
"module_name": "removal",
"enabled": false,
"expiration": "0"
},
"modules": [
{
"module_name": "v3adapter",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "detection",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "infection",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "appcontrol",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "netscan",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "dlp",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "manageability",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "multiscan",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "heuristic",
"enabled": true,
"expiration": "1758036571"
},
{
"module_name": "vulnerability",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "diagnostics",
"enabled": true,
"expiration": "1767281371"
},
{
"module_name": "deviceinfo",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "addon",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "driver",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "removal",
"enabled": true,
"expiration": "1769873371"
},
{
"module_name": "advancedbrowser",
"enabled": true,
"expiration": "1769873371"
}
],
"user": {
"_id": "68c92048c1c57200172d67fd",
"user_id": "68c92048c1c57200172d67fc",
"timestamp": "1758091373",
"email": "sdktest@gmail.com",
"name": "sdk_test_01",
"password": "nopassword",
"licensed": true,
"account_expired": false,
"account_locked": false,
"credentials_expired": false,
"enabled": true,
"roles": ["ROLE_USER"],
"notes": "Test only"
}
}Forge license: AES Encrypt - CyberChef
RPC Interfaces
Check for RPC interfaces with RPC toolkit from Akamai and found nothing:
{
"libwaadbrowser.dll": {},
"libwaaddon.dll": {},
"libwaapi.dll": {},
"libwacollector.dll": {},
"libwadeviceinfo.dll": {},
"libwadlp.dll": {},
"libwadriver.dll": {},
"libwaheap.dll": {},
"libwainfection.dll": {},
"libwalocal.dll": {},
"libwanetscan.dll": {},
"libwaremoval.dll": {},
"libwaresource.dll": {},
"libwautils.dll": {},
"libwavmodapi.dll": {},
"OESISEndpointAssessmentTool.exe": {},
"WaDiagnose.exe": {},
"WaDiagnose_legacy.exe": {},
"wa_3rd_party_host_32.exe": {},
"wa_3rd_party_host_64.exe": {},
"wa_3rd_party_host_ARM64.exe": {}
}Named Pipe Messages Encryption
I used the SDK process ID and 3rd_party, then XORed the two values to get the key. 1/ Convert the number to a string. For example: 46072 → “46072“ 2/ XOR each character of the two strings together. If one string ends, repeat this string, we will repeat this until we can create a 32 byte array. 3/ XOR the array again with 101
Algorithm code:
WAUTIL_RETURN WaCryptoApiFactory::createAESWithTwoNumber(std::shared_ptr<IWaCryptoAES>& aes, wa_int rightNumber, wa_int leftNumber, CryptoApiType type/* = CryptoApiType::Default*/) { WAUTIL_RETURN rc = WAAPI_OK; wa_wstring strRight = string_cast<wa_wstring>(rightNumber); wa_wstring strLeft = string_cast<wa_wstring>(leftNumber); size_t rightSize = strRight.size(); size_t leftSize = strLeft.size(); std::array<BYTE, 32> arr = { 0 }; for (size_t i = 0; i < arr.size(); ++i) arr[i] = (BYTE)(strRight[i % rightSize] ^ strLeft[i % leftSize]); auto key = runtimeXOR(arr, WA_KEY_XOR); return createAES(aes, key, type); }
Resources
BCrypt
- Performing AES GCM using Windows API | by Pratik Chowdhury | Medium
- BCryptOpenAlgorithmProvider function (bcrypt.h) - Win32 apps | Microsoft Learn
- BCryptImportKey function (bcrypt.h) - Win32 apps | Microsoft Learn
- BCryptDecrypt function (bcrypt.h) - Win32 apps | Microsoft Learn
- BCryptVerifySignature function (bcrypt.h) - Win32 apps | Microsoft Learn
- BCRYPT_KEY_DATA_BLOB_HEADER (bcrypt.h) - Win32 apps | Microsoft Learn
DLL Hijacking
- Windows/x64 - PIC Null-Free Calc.exe Shellcode (169 Bytes)
- Windows 11 x64 - Reverse TCP Shellcode (564 bytes)
- Windows/x64 - Dynamic NoNull Add RDP Admin (BOKU:SP3C1ALM0V3) Shellcode (387 Bytes)
COM Hijacking COM
- The Key to COMpromise - Pwning AVs and EDRs by Hijacking COM Interfaces, Part 1 — Neodyme
- The Key to COMpromise - Abusing a TOCTOU race to gain SYSTEM, Part 2 — Neodyme
- The Key to COMpromise - Downloading a SYSTEM shell, Part 3 — Neodyme
- The Key to COMpromise - Writing to the Registry (again), Part 4 — Neodyme
- CoCreateInstance function (combaseapi.h) - Win32 apps | Microsoft Learn
- DllGetClassObject function (combaseapi.h) - Win32 apps | Microsoft Learn
Để ngăn ngừa COM Hijacking:
- Check signature của DLL
- Sử dụng đường dẫn tuyệt đối nếu được
Named Pipe Impersonation named-pipe privilege-escalation
- Windows NamedPipes 101 + Privilege Escalation | Red Team Notes
- MinatoTW/NamedPipeImpersonation
- cyberark/PipeViewer: A tool that shows detailed information about named pipes in Windows
- zeze-zeze/NamedPipeMaster: a tool used to analyze and monitor in named pipes
- Windows API and Impersonation Part 1 - How to get SYSTEM using Primary Tokens | zc00l blog
- Windows API and Impersonation Part 2 - How to get SYSTEM using Impersonation Tokens | zc00l blog