Hooking OpenSSL Functions
About how it hooks OpenSSL functions.
Without hooking, the function (SHA256_Final) has the following instructions:
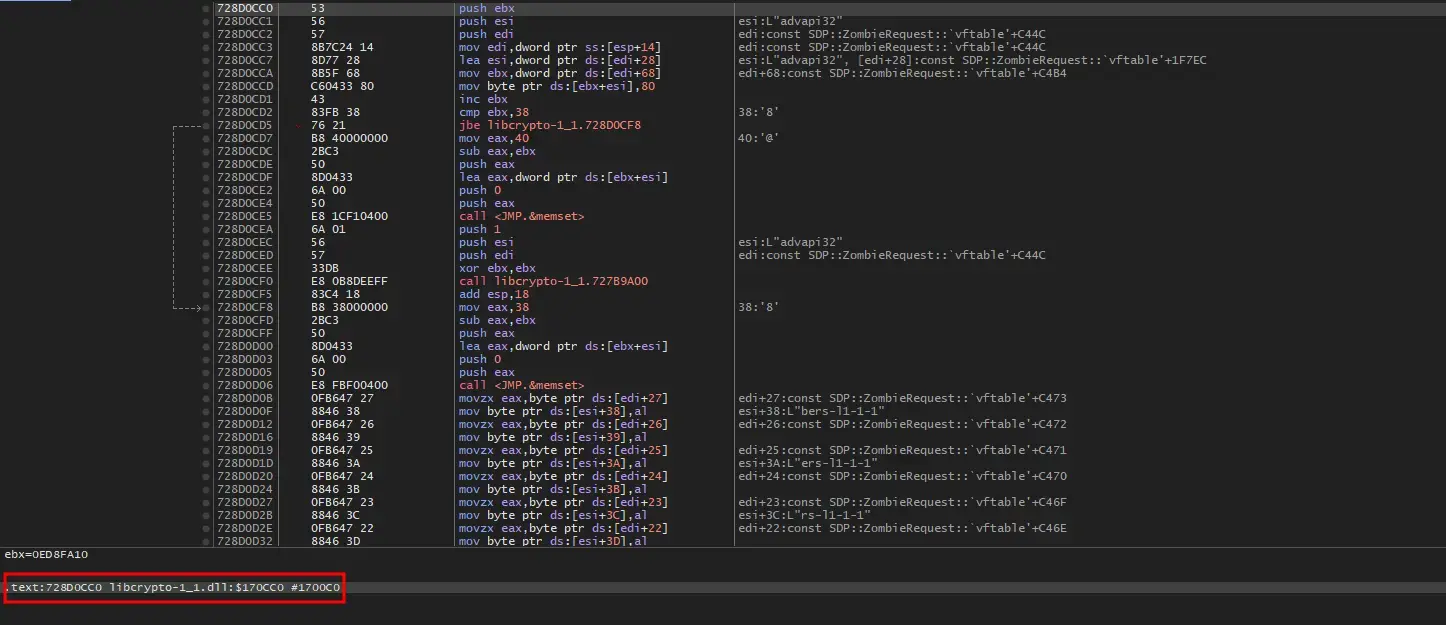
As expected, the first instruction of the function is replaced with an unconditional jump (which is same technique with Detours library):
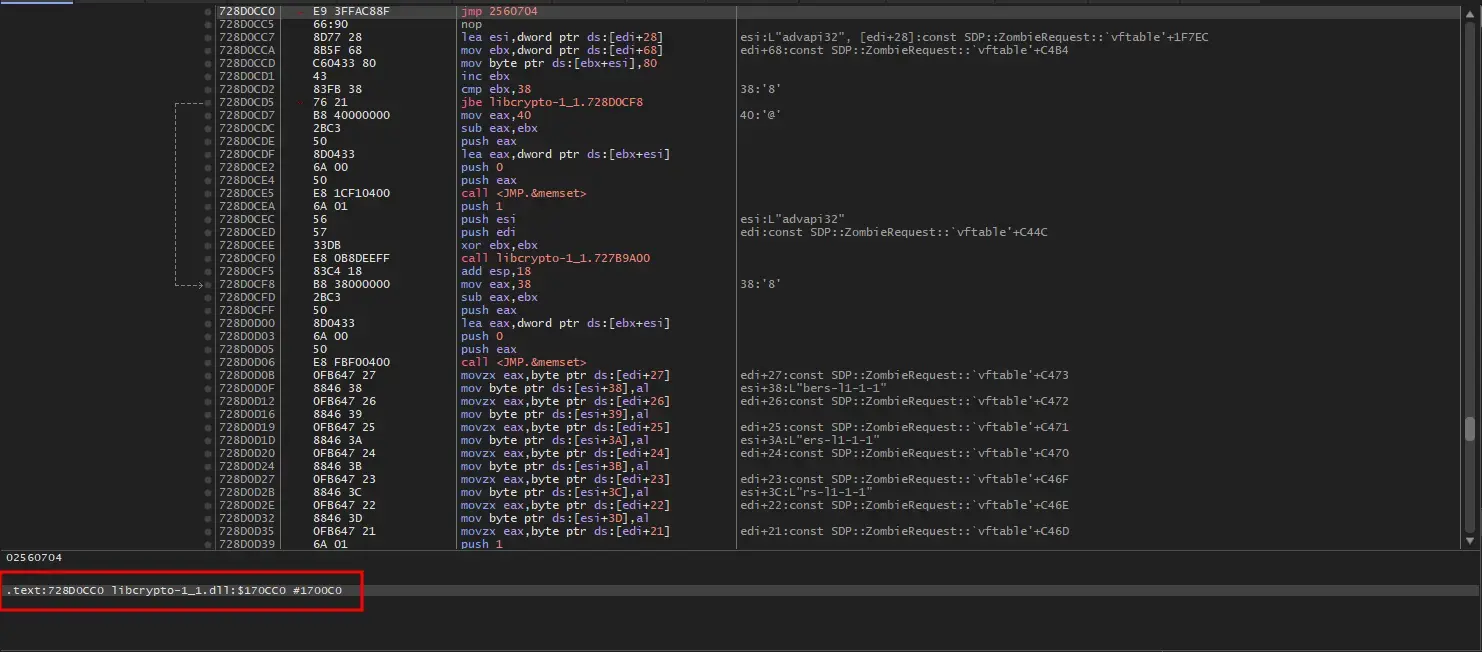
When navigating to the address specified in the jump, I found the trampoline funtion near that place:
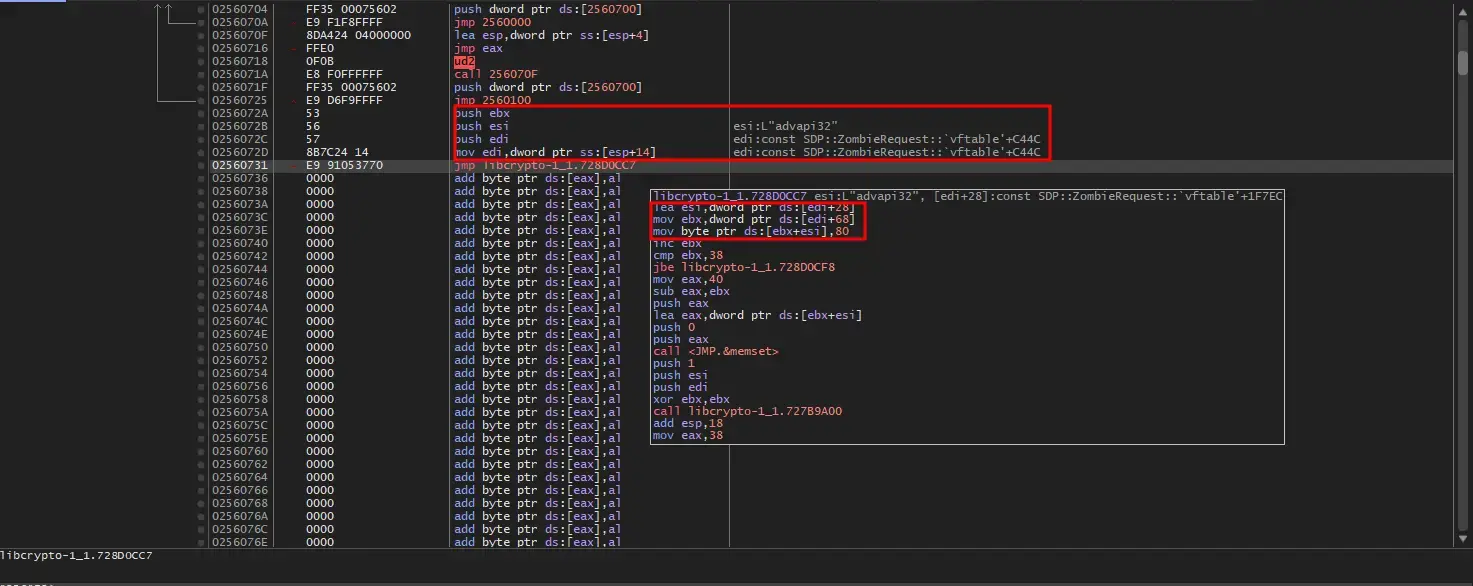
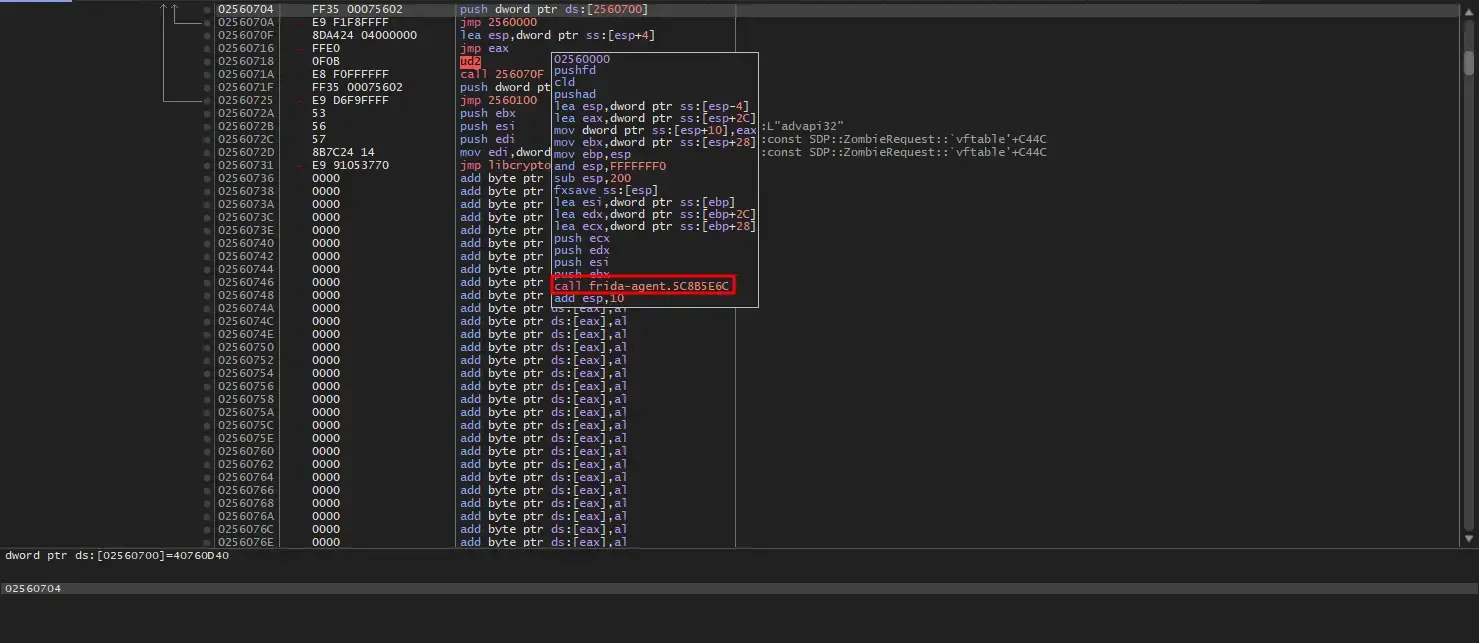
Maybe the addresses in both jmp instructions are Frida-related functions or detours functions:
Tip
We can go to the previous location in x64dbg by pressing the
-key.
Anti-Hooking
I found some ways for preventing hooking with framework like Frida:
- Identify how frameworks conduct hooking (by analyze its artifacts) and obfuscate (patch) the instructions dynamically. For example, with aarch64 architecture, if we use both
x16andx17registers at the function’s prologue, Frida will fail to hook (read the mentioned source code of Frida and O-MVLL in Anti-Hooking | O-MVLL Documentation for more details). However, this approach can be circumvented by patching the obfuscated code one more time and have some more limitation. - DLL unhooking: just restore the original function to eliminate the hooks.