Summary
Chúng ta không thể chống được hết tất cả những mối nguy hiểm mà chỉ nên tập trung vào một số mối nguy quan trọng.
Threat modeling sẽ giúp ta nhận diện và đánh giá được những mối nguy hiểm cho các thành phần của hệ thống. Khi thực hiện threat modeling, ta sẽ xây dựng một threat model chứa những mối nguy hại được sắp xếp dựa theo một tiêu chí nào đó.
Ngoài ra, việc biết được thông tin của đối thủ cũng là rất cần thiết vì khi đó ta có thể thu hẹp phạm vi bảo vệ, giúp tiết kiệm thời gian và chi phí.
How Do We Evaluate Risk?
- For the most part, people suck at accurately evaluating risk.
- When we’re evaluating risk (consciously or unconsciously), we’re influenced by many factors, including whether we feel we are in control.
- That is, human psychology affects how we understand risk.
Everything we do in trying to protect our infrastructure, our services, has to do with human components
- Your attackers are people, too.
- They have their own motivations and are, just like you in your defense capabilities, restricted by constraints or resources.
- Attackers also constantly perform a cost-benefit analysis to evaluate whether a given attack vector is suitable for them.
But What Exactly is a Threat Model?
- Differentiate between threats we can and threats we cannot defend against; threats we care about, and threats we do not care about.
- Wait, what? Can’t we just go and Secure All The Things? Well, it turns out that when you are operating under the wrong threat model, you may actually make things worse.
Question
Why operating under the wrong threat model, we may actually make things worse?
- The above statement’s explaination is in this article Threat Modeling, or Architectural Risk Analysis.
- Threat modeling is figuring out what you can defend against whom.
A concept is stronger than a fact
- Threat modeling is conceptual, it’s a bit abstract, takes some practice, but ultimately leads to a change in frame of mind that helps you cut through a bunch of bullshit and focus on what actually matters.
- It does not tell you “SSLv2 is bad, mmkay?” but rather “weak protocols may be an issue if your adversaries have the capabilities and means to break them”.
Performing the abstract thought exercise of threat modeling restricts your scope and helps you break your larger system into better understood components, since you can’t just have a single threat model for your entire system.
Let us consider an example, here’s a web service:

We probably have some firewalls and network ACLs (Access Control List). By the way, all of this is probably running on somebody else’s hardware aka “The Cloud”, and despite all that the easiest way in is still somebody phishing your employees.
Are we secure yet?
- How on earth do we secure all these things? Of course, it’s impossible to accomplish absolute security here. So let’s try to simplify, to focus. What is it we’re trying to protect? What are our assets?

- Let us consider your actual end-user data your primary asset. To ensure it’s not accessed without authorization, we require some sort of authN/authZ system that allows us to cross the trust boundary.
- Trust boundaries show where a level of trust changes to either elevated or lowered levels of trust. Identifying your trust boundaries helps you clarify which components likely have a similar attack vectors, similar threat models.
Focusing only on the data as the primary asset, we can now identify different vulnerabilities in our system to see how somebody could gain access.
- One method of categorizing vulnerabilities is the STRIDE model, which maps threats to system properties.

- Focusing on one property, we can the identify the different vulnerabilities. As you can tell, some of these shift the focus onto another system component, such as the authN/authZ system.

But identifying vulnerabilities alone is not enough; we also need to assign them a threat score to figure out which ones are more important to us to defend against.
- One method to calculate threat (or risk) scores for each attack vector and vulnerability is called DREAD, which lets you assign a numeric value to each of the attack’s Damage, Reproducibility, Exploitability, Affected Users, and Discoverability.
- I tend to add a second “D” (Detection): how hard is it for the defender to discover the compromise.

- You can then assign values to each vulnerability based on these factors and the value of the asset.

- The resulting scores should give you an idea on which areas you should focus on.
You Need to Know Your Adversaries
- Attackers will continue to employ the cheapest, most effective attack until it ceases to be that.

- The more time and effort they have to spend on an exploit, the less likely they are to continue to use it. Raising the cost of an attack is therefore a great way.
- But it’s not the only way. Sometimes your smartest move is not to implement bigger and better defenses, but to lower the value of the asset.
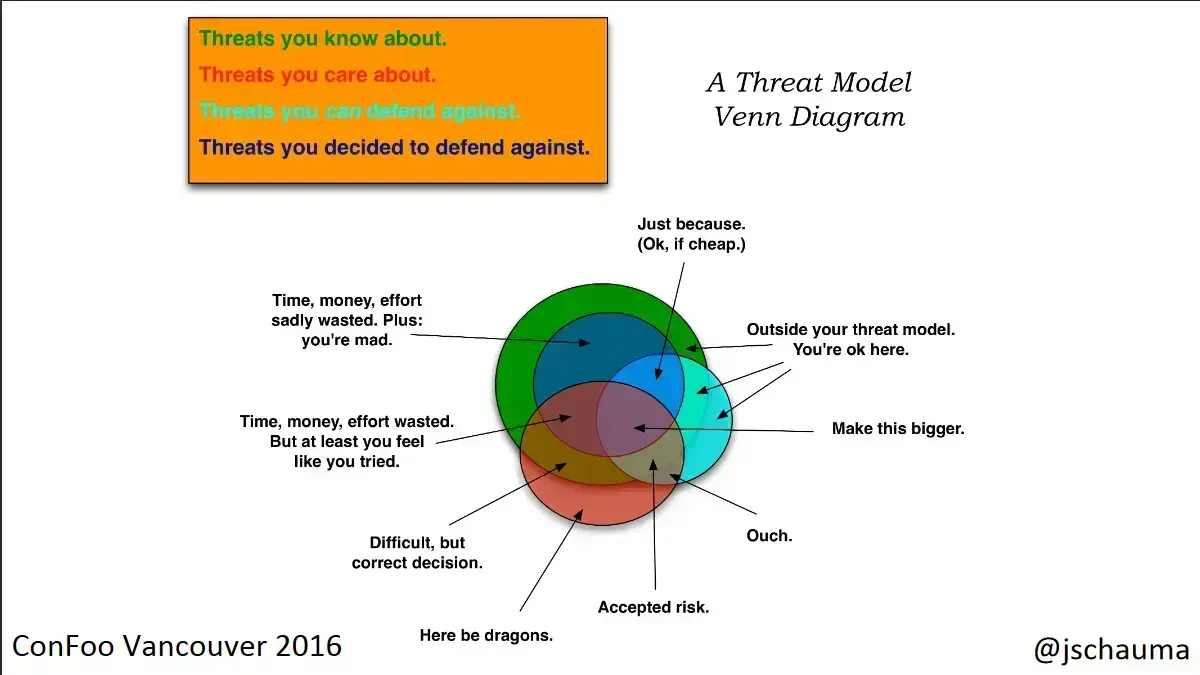
The Venn Diagram
Alright, so let’s look at this Venn diagram again, building it up as we go along
- First of all, there are threats that we know about.
- Of those threats, there are some that we care about, and some we do not care about.
- Next, there are some threats that we can defend against. This is the tricky part: we have to be honest with ourselves and decide, consciously, what our defensive capabilities are.
Threat Modeling Process
To summarize our threat modeling process:

Some Good Rules to Keep in Mind
- Your adversaries are people, too. They will make rational decisions as they pursue their goals. Understand their goals and objectives, and you can better focus your defenses.
- You can’t secure all the things. You need to prioritize.
- There are two ways to make an attack less profitable for the attacker: raise the cost of the attack or lower the value of the asset.